Data Protection Solutions: Keep Your Business’s Data Secure
Data protection is a process or set of controls used to protect data from unauthorized access. Data can be leaked or stolen in many ways, including employee mistakes, breaches, cyberattacks, or data dumps, and businesses need data protection solutions to protect their data from accidental leaks or theft. An insufficient data protection solution can put a business at risk of data loss, theft, or reputation damage.
There are several data protection solutions available, including data encryption, data masking, data anonymization, and data destruction. Proxies are also a data protection solution that can help keep data safe.
This article will discuss cyber threats, why data protection is important, and how to get data protection on demand through a data protection proxy. You can use the table of contents to refer back to a section or skip to what is most relevant to your needs.
What Are Cyberattacks and Cyber Threats?

When someone hacks into a computer or network to get information, like passwords or credit card numbers, it is called a cyberattack. This stolen data is wrongfully used to steal money, data, and people’s identities. There are all sorts of cyberattacks, and they can affect people and businesses in different ways. Here are a few of the most common:
Ransomware
Ransomware is a type of malware that encrypts files on a user’s computer, then demands payment to restore access. This can be devastating for businesses and individual users, as important files may be lost forever if the ransom is not paid.
There have been several high-profile ransomware attacks in recent years, including the WannaCry attack in 2017 and the NotPetya attack in the same year.
Ransomware is typically spread through phishing emails or malicious websites. Once a user’s computer is infected, the ransomware will encrypt important files and display a message demanding payment to decrypt the files, usually in cryptocurrency like Bitcoin.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

Phishing
This is when a hacker sends you a fake email or text message that looks like it’s from a trusted source, like your bank or credit card company. The goal is to trick you into giving away your personal information.
Phishing can have serious implications for both personal and business users. Phishing can result in the theft of personal information, such as passwords and credit card numbers, leading to identity theft and other financial losses.
For businesses, phishing can lead to the theft of customer data or trade secrets. This can have a devastating impact on a business, leading to lost revenue and even bankruptcy. Businesses can also be held liable for any losses suffered by customers as a result of a data breach.
DDoS attacks
A DDoS attack is when a hacker overloads a server with requests, causing it to crash. This can prevent legitimate users from accessing the site or service, leading to lost revenue and customers.
Businesses are affected in many ways by DDoS attacks. One of the most common outcomes is having their website or online services taken offline. This can result in a loss of revenue for the business, as customers may not be able to access the website or services.
Additionally, businesses may incur costs associated with repairing or rebuilding their website or online services after a DDoS attack.
DDoS attacks can also result in a loss of customer data. This can include customer names, addresses, credit card numbers, and other sensitive information. Additionally, businesses may lose confidential data, such as trade secrets or competitive information.
What Is Data Protection?

Data protection involves taking steps to safeguard data from unauthorized access, use, disclosure, alteration, or destruction. Data protection is important because businesses rely on data to operate. When data is leaked or stolen, it can cause an organization to lose money and customers or even go out of business. Cyberattacks don’t just put your customer’s data at risk; your business strategies and trade secrets could also be exposed.
Luckily, there are many ways a business can protect data. Some common data protection methods include data encryption, data masking, data anonymization, and data destruction.
Data encryption is a data protection solution that involves transforming data into an unreadable format for unauthorized individuals. When encrypting, sophisticated algorithms convert data into unreadable text or ciphertext.
A decryption key is needed to unlock the data and make it readable again. The key can be a password or a code, and only authorized individuals with the key can access the data. Unsurprisingly, encryption is one of the most common and effective data protection solutions available.
Meanwhile, data masking obscures sensitive data so that it can’t be easily read. Also known as data obfuscation, data masking protects data by hiding the original data with modified content. This makes it tough for unauthorized users to access the data. Masking is often used to protect personally identifiable information (PII) or commercially sensitive data. The types of data masking include:
- Static data masking
- Dynamic data masking
- On-the-fly data masking
Anonymization is a data protection solution that removes identifying information from data so that it can’t be traced to an individual or organization. It protects data subjects’ privacy and prevents discrimination. Anonymized data isn’t linked to any data subject.
However, it’s important to note that there is no such thing as perfect anonymity and that it’s always possible to connect anonymized data with its source if enough information is known. Even so, data anonymization is a common and effective data protection solution for protecting data subjects’ privacy.
Through the process of pseudonymization, real data is replaced with fake data. This makes it hard for unauthorized users to connect the data to an individual or organization. Pseudonymized data is still linked to the data subject, but the link is not easily traceable.
There’s also tokenization, which is a process of replacing sensitive data with nonsensitive data called tokens. Tokenization can be used to protect credit card numbers, social security numbers, and other PII.
Data archiving is the act of storing data in an offline or online storage system. This means that the data is not accessible through the network. Data archiving can be used as a data protection method because it protects the data from being accessed by unauthorized users. It also protects the data from being modified or deleted by unauthorized users.
Finally, data destruction permanently destroys data so that it can’t be recovered. Data destruction can be physical or digital. Physical data destruction is when someone destroys data storage devices such as hard drives, CDs, and USB flash drives.
Digital data destruction, on the other hand, involves deleting data using special software or formatting a drive so that it can’t be used again. Both means make the data impossible to recover.
Key features of data protection solutions
Several key features make data protection solutions essential for businesses of all sizes. Here are some of the most important:
- Data backup and disaster recovery: In case of a system crash or data loss, a data protection solution can help you quickly recover your critical data. It provides a way to recover lost or recovered data and restore your system after a crash or other major disaster.
- Encryption: Data protection solutions can encrypt your data to prevent unauthorized access. When data is converted into an unreadable format, unauthorized users can’t compromise it, which ensures the privacy of your communications. It also helps maintain the confidentiality of your files and documents, as well as your online transactions and wireless connections.
- Access control: Data protection solutions can control who has access to your data and what they can do with it. Access control systems can be either physical or electronic. Physical access control systems use locks, gates, and other physical barriers to control access to a particular area. Electronic access control systems use cards, codes, or other electronic means to control access.
- Activity monitoring: Data protection solutions can monitor activity on your systems to help you identify potential threats. By tracking user activity, you can see which employees are accessing sensitive information and determine if any unauthorized access has occurred. You can also identify which files or folders are being accessed the most, so you can take steps to protect them from unauthorized access.
- Compliance: Data protection solutions can help you meet industry regulatory requirements. Compliance can help ensure that data is properly managed, controlled, accessible only to those with a legitimate need, and properly disposed of when no longer needed, preventing unauthorized individuals from gaining access to sensitive information.
- Peace of mind: Knowing that your data is protected can give you peace of mind and help you focus on other aspects of your business. Ensuring that your data is encrypted and backed up regularly can help. So will good customer support if you have any questions about your data protection solutions or need help troubleshooting a problem. Having efficient data protection solutions in place will assure you that your data is well-protected even as you appreciate that you’ll always have access to it.
Why is data protection important?
Data is a valuable asset, and that’s why data protection is needed. Businesses use data to make decisions, operate their businesses, and serve their customers. Data can be used to improve products and services, understand customer needs and wants, make better decisions, and protect trade secrets. For example, you don’t want sensitive business data from your competitors’ hands because it could give them an advantage.
Data protection is also important because data breaches can be costly. There are several types of data breaches that businesses can face. One is a malicious attack, in which someone deliberately hacks into a company’s computer system to steal or destroy data.
A second type is a system failure, in which the computer system crashes or malfunctions and accidentally exposes sensitive data. Data breaches are also caused by careless mistakes, where a member of the company accidentally emails or prints confidential information and sends it to the wrong person.
Lastly, a business can be targeted by cybercriminals who use phishing schemes to trick employees into revealing their login credentials or other sensitive information.
You must ensure your business doesn’t fall victim to data breaches to avoid costly legal ramifications and damage to your business’s reputation. Remember, there are legal penalties attached to data breaches.
The hefty fines handed down by data protection authorities can affect your business as much as the legal costs associated with recovering from data breaches. In some cases, data breaches can also lead to jail time.
How Big Is the Data Protection Market Opportunity?

According to Straits Research, the global big data security market is projected to reach $115 billion by 2030, up from the $24 billion it was worth in 2021.
The expansion of this market is driven by factors such as the fast adoption of digital technologies, rising concerns about data privacy and security, and the increasing role of data-based trend analysis methodologies. However, the lack of awareness about data protection solutions and services among small and medium-sized enterprises (SMEs) is restraining the growth of this market to a certain extent.
The data protection market includes data backup and recovery, data encryption, and data erasure/disposal. It also boasts professional and managed services such as consulting, integration and deployment, and support and maintenance. The sector’s growth is due to the ever-increasing need to protect mission-critical data from accidental or intentional deletions, hardware failures, and software corruptions.
How To Get Started With Data Protection in Your Business

There are many ways to jump-start data protection in your business. The most important thing is to have a plan that will work for your specific business needs. Here are a few tips to get you started:
- Determine what type of data you need to protect. This includes both internal and external data.
- Put together a team that will be responsible for data protection. This team should include IT staff and employees from other departments such as marketing or accounting.
- Develop a data protection policy. This policy should outline how data will be protected, who will have access to it, and what security measures will be put in place.
- Implement the data protection policy. This includes training employees on the policy and ensuring that all systems and data are secure.
- Monitor the data protection policy. Regularly review the policy to make sure it is still effective and revise it as needed.
How to set up a data protection solution
Once you have decided on a data protection solution, there are a few steps you need to take to set it up and get started protecting your data as soon as possible:
- Choose a data protection solution that fits your needs. There are a variety of data protection solutions available, so it is important to choose one that will work best for you and your business.
- Purchase the data protection solution. This can be done through various sources, such as online retailers or data protection solution providers.
- Install the data protection solution. This process will vary depending on the data protection solution you have chosen, but most can be installed quickly and easily.
- Configure the data protection solution. This process will again vary depending on the data protection solution you have chosen, but most solutions offer a variety of options that can be customized to fit your needs.
- Protect your data. Once the data protection solution is installed and configured, you can begin protecting your data.
By following these steps, you can be sure that your data is protected and secure. Data protection is an integral part of any business, so it is important to choose a solution that fits your needs and provides the level of protection you need.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

How else can you protect yourself from cyber threats?
There’s no question that knowing how to ensure data protection is a real concern for both individuals and businesses. As cybersecurity threats are becoming more and more sophisticated, there’s a pressing need to be vigilant in protecting ourselves. If you’re running a business (or otherwise), here are some tips you will find useful:
- Educate employees on cybersecurity risks and best practices. Employees are often the weakest link when it comes to cybersecurity. They may unknowingly click on a phishing email or download a malicious attachment. By educating employees on cybersecurity risks and best practices, businesses can help reduce the likelihood of a successful cyberattack.
- Implement strong security measures. Businesses should implement strong security measures such as firewalls, intrusion detection/prevention systems, and data encryption. These measures can help to deter cyberattacks and make it more difficult for attackers to access sensitive data.
- Keep software and systems up to date. Outdated software and systems are often more vulnerable to attack than up-to-date ones. Businesses should ensure that all software and systems are kept up to date with the latest security patches.
- Back up data regularly. Businesses should back up their data regularly to ensure that they can recover from a cyberattack. Data backups should be stored offline in a secure location.
- Monitor activity on networks and systems. Businesses should monitor activity on their networks and systems for signs of a possible cyberattack. They should also have procedures in place for responding to a cyberattack.
- Use a VPN. A virtual private network (VPN) can help protect businesses’ data as it travels over the public internet. VPNs encrypt data, making it more difficult for attackers to intercept and read it.
- Use a proxy. Businesses can help protect their internal network from direct attacks by using a proxy server. Proxy servers act as a buffer between internal networks and the internet, making it more difficult for attackers to gain access.
What is a proxy?
Proxies are intermediary servers that act on behalf of other computers or devices. In short, a proxy is a middleman between you and the internet.
Sometimes people will use the terms “proxy,” “proxy servers,” or “proxy IP addresses” interchangeably. However, proxy servers are the physical or virtual machines that contain proxy IP addresses. Most people usually mean these IP addresses when they search online for proxies or proxy servers.
Proxies are used for various reasons, such as to improve performance, reduce costs, and increase security. But in this context, we’ll focus on how proxies can be used for data protection.
How do proxies protect data?
So, how does proxy-oriented big data protection work? Proxies protect data in several ways. They provide anonymity, privacy, and security. You can better control how your data is accessed and used by rerouting data requests through a proxy server.
Proxies can enhance your privacy and anonymity by disguising your IP address and location. When you use a proxy, the proxy server replaces your IP address with its own IP address. This makes it difficult for anyone to track your activities or identify you.
A proxy can also help you remain anonymous online by hiding your browsing data. When you browse the internet, your browser stores data about the websites you visit in a history file. This data can be used to track you and build a profile of your activities. However, when you use a proxy, the data is hidden, making it more difficult to track your movements online.
Additionally, proxies can help protect your data from being monitored or intercepted. By routing data through a proxy server, you can increase the security of your data and make it more difficult for hackers or other malicious individuals to access it. That’s because proxies enhance data security by blocking unwanted or malicious traffic, such as DDoS attacks or malware.
Proxy servers receive requests for data from devices such as computers and smartphones. The proxy server then accesses the internet on behalf of the device and returns the requested data.
Proxies can switch between IP addresses and not limit you to one physical location. Location switching is another valuable tool for hiding your identity and online activity.
Proxies and scraping
Web scraping, also known as data scraping, is a process in which a scraper (such as Rayobyte’s Web Scraping API) extracts data from a website. This is done for various reasons, including analyzing data, gathering data for a research project, or creating a database of information that users can examine.
One of the main benefits of using proxies when scraping is that they can help obscure your IP address and keep your identity hidden.
They can also protect you from being blocked by the website you are scraping. Most websites will block IP addresses associated with data scraping activities to prevent their site from crashing due to bot traffic. They may also set a “crawl rate,” which is the rate at which a program can make requests to a website. If a program makes too many requests in a short period, the website may assume it is a data scraper and block the IP address.
Proxies can help you get around these blocks by making it appear as if the requests are coming from different IP addresses. This will help you scrape data more effectively and efficiently.
What are the different types of proxies?
There are many types of proxies, including data center proxies, ISP proxies, and residential proxies. Proxies can also be IPv4 or IPv6, HTTP, HTTPS, SOCKS, dedicated or semi-dedicated (shared), or rotating and transparent proxies. It’s also worth noting that proxy servers can be software-based or hardware-based.
The many types of proxies can get confusing for people new to proxies. What’s more, these proxies can and often do overlap, which is why you might find there are dedicated IPv6 data center proxy servers or rotating HTTP IPv4 proxies. It’s beyond the scope of this article to discuss all the types of proxies that exist. We’ll focus on three:
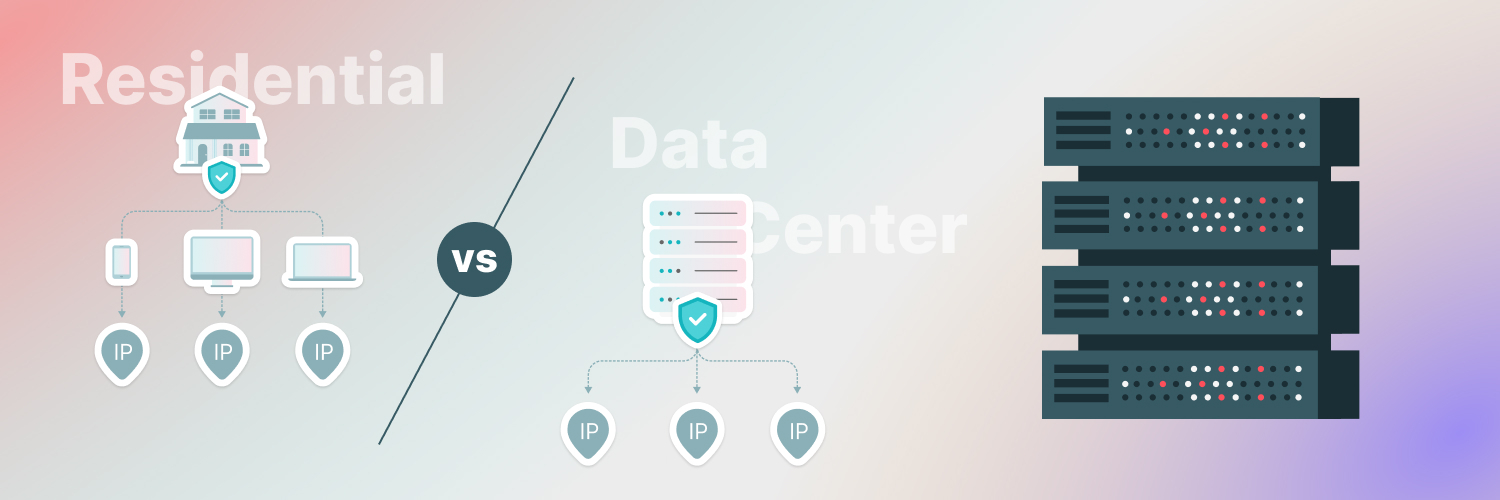
Residential proxies
Residential proxies are IP addresses provided by internet service providers (ISPs). ISPs assign these IP addresses to physical locations at a city or country level, such as the IP address assigned to a home router or your business.
Because residential proxies are real IP addresses assigned by ISPs, they offer the highest level of anonymity. That’s because it’s difficult to determine if it’s a person or bot behind a residential IP address.
Furthermore, residential proxies are not commonly used for malicious purposes, so they’re less likely to be flagged by security systems. That’s why websites usually don’t ban residential proxies — because they’re seen as legitimate traffic.
Data center proxies
Data center proxies are IP addresses that aren’t assigned by an ISP. Instead, data center providers issue them. Because data center proxies are not associated with any physical location, they’re less anonymous than residential proxies. You can hide your IP address by using data center proxies, but websites easily identify traffic coming from a data center.
Moreover, data center proxies are commonly used for scraping or spamming. Naturally, spamming is a malicious use case. As a result, they’re more likely to be banned by websites and security systems. Data center proxies also tend to have slower connection speeds than residential proxies.
ISP proxies
ISP proxies are a hybrid of residential proxies and data center proxies. They used to be called static residential proxies, and they were created by taking data center IP addresses and registering them with autonomous system numbers (ASNs) associated with ISPs.
By associating data center IP addresses with ASNs, they appear to be residential IPs. As a result, ISP proxies offer increased anonymity and are less likely to be banned by websites. They also boast faster connection speeds than are possible with shared or peer-sourced proxies.
How to set up proxies
Now that we’ve told you the purpose of data protection and learned a little more about proxies, let’s look at how to set them up. Understanding how to set up proxies will help you improve your experience by ensuring you always have a solid connection that helps keep your data safe and secure.
Because there are multiple types of proxies and various ways of configuring them, different settings might be needed when setting up. Therefore, it’s imperative to know the type of proxy you’ll use.
Because data center proxies are more likely to get blocked than residential ones, you can opt to set them up to rotate. On the other hand, residential proxies can be set up in static or rotating forms.
Setting up proxies on your network
Proxy providers typically give users a list of IP addresses and port numbers. To set up a proxy on your network, simply go to your network settings and enter the IP address and port number into the appropriate field.
Alternatively, you can go to your browser’s settings and paste the provided IP address into the proxy field.
You should now be able to use your proxy to surf the web, download files, and more. To check whether you’re actually using your proxy and not your default IP address, go to a website such as IPLeak.net and check the displayed IP address. You could also use your browser to search “What’s my IP address?” If the result matches the proxy’s IP address, then you’re good to go!
Just remember to keep your ports straight, so you’re always using the right proxy for the right traffic.
If you don’t wish to use your proxy, you can simply disable it by going back into your network settings. While there, remove the IP address from the proxy field, or select the “Off” or “No proxy” option.
Enabling your proxy
The minute you’ve set up your proxy on your network, you can enable it via your provider. This process is crucial for preventing nonauthorized users from using your proxies to connect to the internet. It’s also a great way to keep your data safe and your proxies secure.
There are three types of authorization available depending on the ports you use. These are:
- IP Authorization: Only allows a set number of IP addresses to use a proxy. The connection will be denied if an unauthorized IP address tries to access the internet through the proxy.
- User/Password Authentication: This type of authorization requires a username and password before a connection can be made.
- SOCKS: A SOCKS authorization requires a SOCKS username and password to initiate a connection.
Once you’ve chosen the type of authorization you want to use, simply enter the required information into your proxy provider’s dashboard. You can now rest assured that only authorized users will be able to use your proxies!
Depending on your provider, you may have to enable one or all of these authorization types. If you’re not sure which one to use, simply contact your provider, and they should be more than happy to help you out.
How To Find the Best Data Protection Solution for Your Business

The first step is to identify your organization’s specific needs when it comes to data protection. What are the types of data you need to protect? How much data do you need to protect? What are your compliance requirements? Once you have a good understanding of your organization’s specific needs, you can begin to research the various solutions that provide data protection on demand.
You’ll want to consider various factors when choosing a data protection solution. The first is the level of security the solution offers. You will want to make sure that the solution you choose provides the level of security your organization needs. The second factor is ease of use. You’ll want to ensure that the solution you choose is easy to use and has features that will benefit your organization.
The third factor is the cost. There are various proxy-oriented big data protection solutions available, and the cost will vary depending on the features and level of security offered. It’s important to compare the cost of different solutions to find the one that fits your organization’s budget.
Once you’ve considered all these factors, you can begin to narrow down your options and choose the best data protection solution for your organization. It’s important to consult with experts who can help you understand the different options available and choose the one that’s right for your organization.
By taking the time to understand your organization’s specific needs and researching the different solutions available, you can find the best Big Data protection solution available for your organization.
Final Thoughts

Data is a valuable commodity, and it needs to be protected from things like DDoS attacks or accidents like employee leaks. We’ve looked at why data protection is important for your business. Protecting your data can mean the difference between a successful business and a failed one.
Fortunately, proxies can help with data protection by:
- Providing a secure gateway between users and the internet
- Protecting internet users’ IP addresses
- Keeping internet users anonymous
- Making it safe for anyone to use the internet
By embracing the use of proxies, your business can rest assured that its data is safe and sound, no matter what threats may come your way.
When it comes to web scraping for critical business data, in particular, proxies are a must. They provide a secure gateway between users and the internet, protecting users’ IP addresses and keeping them anonymous.
Proxies can also help businesses bypass bandwidth limits imposed by their ISP or data center. This ensures that businesses can scrape as much data as they need in a timely manner without experiencing any bottlenecks.
To sum it up, proxies are a great way for businesses to protect their data from DDoS attacks, employee leaks, and other threats. They provide a safe and secure way for businesses to browse the internet and conduct critical web scraping activities without worrying about being detected or tracked.
What data protection solution should you choose?
Rayobyte is a reliable and affordable proxy provider that offers a wide range of proxies to suit your needs. We have an extensive network of residential, rotating ISP, data center, mobile, and ISP proxies across various countries. This gives you a wide selection of IP addresses to choose from, so you’re sure to find a working IP address for your needs.
Want to explore a proxy-oriented big data protection solution? Our proxies are also compatible with a wide range of applications and websites so that you can use them for various tasks. And if you need help setting up or using our proxies, our friendly customer support team is always happy to assist you.
Get in touch with Rayobyte today to learn more about our proxy services and how we can help you get started protecting your data.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.