Bluetooth Proxy Security (How To Connect Devices Safely)
One of the most frustrating things about technology is the piles of wires you have to deal with. Even when you try to keep them organized, they somehow find a way to get impossibly tangled. To deal with this problem, many companies have started developing and manufacturing wireless devices that use Bluetooth technology. This means the majority of your devices can connect to your headphones, computer, phone, speakers, or whatever else you need without a wired plug-in. However, this also means that as tech consumers, we need to be more attuned to the issue of Bluetooth security.
Making sure your Bluetooth fitness tracker doesn’t get hacked is as simple as getting a Bluetooth proxy. The more Bluetooth devices we accumulate, the more important it is to have a method of keeping them secure. There are so many different ways that hackers can weaponize Bluetooth for hacking purposes, but it can be really simple to stay one step ahead of those hackers. Click around our table of contents to get the best tips to enhance your Bluetooth security and keep hackers out.
Table of Contents
2. How to Prevent Bluetooth Hacking
4. Finding the Best Tools for Bluetooth Security
Is Bluetooth Secure?
![]() Since Bluetooth is so convenient and widespread, you probably wonder if Bluetooth is safe from hackers. The problem is that it is so convenient and easy to use for everyone, so people have figured out how to hack it. In order to get connected to Bluetooth devices, your personal device that is Bluetooth-enabled has to have a radius of about thirty feet. This means if someone looking to launch cybersecurity attacks (or just mess with you) is nearby, you might have a hack-induced headache coming for you. You want to be able to go for a run and connect your heart rate tracker with Bluetooth, without worrying about a potential bank hack.
Since Bluetooth is so convenient and widespread, you probably wonder if Bluetooth is safe from hackers. The problem is that it is so convenient and easy to use for everyone, so people have figured out how to hack it. In order to get connected to Bluetooth devices, your personal device that is Bluetooth-enabled has to have a radius of about thirty feet. This means if someone looking to launch cybersecurity attacks (or just mess with you) is nearby, you might have a hack-induced headache coming for you. You want to be able to go for a run and connect your heart rate tracker with Bluetooth, without worrying about a potential bank hack.
One of the most common forms of Bluetooth hacking is called BlueJacking—this is when someone uses a Bluetooth device to hijack your phone and send you spam advertising. You’ll end up getting a bunch of annoying messages. Although this is annoying, you have to be careful about it because it can get more insidious. Hackers can use Bluetooth attacks to launch phishing against you, posing as a bank or another trusted source in order to get account or personal information.
BlueSnarfing—another form of Bluetooth hacking—is when an attack takes data from your device, as opposed to sending it to you like BlueJacking. This allows them to collect enough sensitive information from your personal device to further attack your identity security.
BlueSmacking is when someone sends such a big data file that the Bluetooth shuts down, and therefore causes problems for your device. Finally, BlueBugging is when someone uses a “backdoor” for your personal device and spy on all of your online activities on your personal device.
Since Bluetooth devices have to have a unique device identifier, hackers can also use Bluetooth to track your location. Usually the identifier changes, but sometimes it doesn’t, so a hacker can find it again. If you’re wondering how to prevent Bluetooth phone hacks and still be able to use Bluetooth, there are still ways to use your phone safely, and ways to make sure Bluetooth is running effectively without being hacked.
How to Prevent Bluetooth Hacking
 Bluetooth-enabled devices crop up in all sorts of technology these days. Cars even have Bluetooth, so you have to pay extra attention to avoiding hacks. However, there are ways to learn how to secure Bluetooth devices without a ton of extra work or fancy technology. If you’re on the go with your phone and need to access your bank account, you might want to try turning off your Bluetooth capabilities to keep it secure while you enter in your information. If you have to transfer large, personal files over Bluetooth, you should see if you can password-protect them or create some kind of barrier.
Bluetooth-enabled devices crop up in all sorts of technology these days. Cars even have Bluetooth, so you have to pay extra attention to avoiding hacks. However, there are ways to learn how to secure Bluetooth devices without a ton of extra work or fancy technology. If you’re on the go with your phone and need to access your bank account, you might want to try turning off your Bluetooth capabilities to keep it secure while you enter in your information. If you have to transfer large, personal files over Bluetooth, you should see if you can password-protect them or create some kind of barrier.
In general, you should keep your Bluetooth off if you’re not using it. Most devices also let you turn off the ability to discover new devices and let you only pair with things they already “recognize.” These are not fail-safe, of course. A lot of Bluetooth devices need to be Bluetooth-enabled to do what they do, which can cause problems for Bluetooth privacy.
Keeping on top of Bluetooth security is pretty similar to keeping on top of your general Internet security—you can’t take the speed and ease of technology for granted, but there are ways that it can work better for you. Although Bluetooth functions a little differently, a proxy is still a great option for your digital privacy.
Why Use a Bluetooth Proxy?
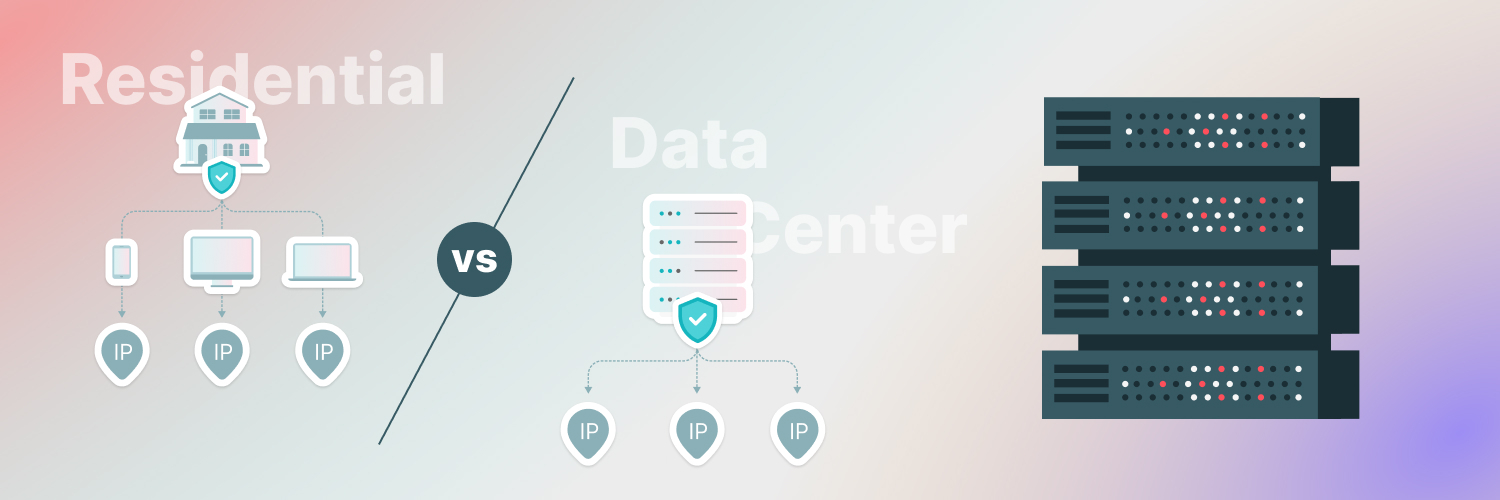
 A Bluetooth proxy provides the same benefits and protection that they give to personal devices like computers, mobile devices, and anything else. For your personal devices that connect to other Bluetooth devices, you should consider using a proxy to protect your personal information and transfer files and data safely. This is especially useful for mobile devices, especially since you probably need to have Bluetooth on for Bluetooth headphones when you’re on the go.
A Bluetooth proxy provides the same benefits and protection that they give to personal devices like computers, mobile devices, and anything else. For your personal devices that connect to other Bluetooth devices, you should consider using a proxy to protect your personal information and transfer files and data safely. This is especially useful for mobile devices, especially since you probably need to have Bluetooth on for Bluetooth headphones when you’re on the go.
Proxies act as a barrier between your personal device and the websites or apps you’re accessing by providing a proxy IP address to mask your device’s IP address. Hackers and malicious actors can’t tie your personal information to your personal device’s IP address. In addition to preventing cyber attackers from tracking you, using a Bluetooth proxy lets you get around geoblocking. IP addresses for all devices have to tether to a specific location, but a proxy IP address lets you put the location wherever you want. Gamers love to use this feature with high-octane video games because they can choose a server near the game server, which cuts down on lag. For those of us using a Bluetooth proxy to surf the Internet freely while still using our Bluetooth devices, this can help us prevent Bluetooth phone hacks.
Proxies also have faster network speeds, especially if you are able to get one where you’re the only user or one of few. This means you can complete big tasks faster and not have to worry about slow transferring time, especially for sending large files over Bluetooth.
You can use a Bluetooth proxy for a computer or mobile device, but there are different proxy protocols that work better with each. A SOCKS proxy is probably best for a phone so you can use certain applications with the SOCKS proxy, while an HTTP or HTTP(S) proxy works better with the majority of websites because it’s the protocol that most websites use. Making sure you have the correct proxy installed isn’t so difficult, especially if you get a proxy from a reputable and helpful provider.
Finding the Best Tools for Bluetooth Security
 When looking into getting a Bluetooth proxy, you’ll probably come across a variety of free or public proxies. These might seem like a good idea so you can try out a proxy before committing to buying one, but we advise against it for a variety of reasons. Free proxies are more susceptible to hacks, and there are likely to be a lot of people using one free proxy together. They sort of function on the honor system, hoping that no one will hack in and steal a ton of data. This is not very dependable and overall negates the purpose of getting a proxy for Bluetooth security.
When looking into getting a Bluetooth proxy, you’ll probably come across a variety of free or public proxies. These might seem like a good idea so you can try out a proxy before committing to buying one, but we advise against it for a variety of reasons. Free proxies are more susceptible to hacks, and there are likely to be a lot of people using one free proxy together. They sort of function on the honor system, hoping that no one will hack in and steal a ton of data. This is not very dependable and overall negates the purpose of getting a proxy for Bluetooth security.
At Rayobyte, we offer a variety of proxies to best suit customer needs. We also have 24/7 customer service to address any issues as they come up. There a few different options for a proxy for Bluetooth security: dedicated, semi-dedicated, and rotating. A dedicated proxy is one proxy IP address for your personal device, specific to you and only you. This is great for a customer who needs coverage and doesn’t want to be compromised by sharing a proxy.
On the other hand, a semi-dedicated proxy is a good money-saving option, and it’s only shared between three to five users. With a reputable provider like Rayobyte, you can rest easy in that your Bluetooth privacy won’t be compromised by sharing a proxy.
Finally, for the people who want major Bluetooth security, there are rotating proxies. This is a series of rotating proxy IP addresses that switch out as often as you need them to. This is a good option for people doing highly sensitive work, like reporting and interviewing sources who need protection. You want to make sure you can collect all your data and never have it traced or compromised.
Final Thoughts
 Using a Bluetooth proxy ensures you won’t have to be constantly checking your Bluetooth device and worrying about it. Since every device is turning to wireless these days, it’s important to understand Bluetooth and protect your personal devices from being compromised. The convenience that new technology brings also means that it can be easier to hack in some ways. However, these products are all easy enough to use that even those of us without Computer Science degrees can stay on top of our Bluetooth security. Guaranteeing your safety online only takes a few steps, and using a good proxy is the perfect way to make sure your personal information stays safe.
Using a Bluetooth proxy ensures you won’t have to be constantly checking your Bluetooth device and worrying about it. Since every device is turning to wireless these days, it’s important to understand Bluetooth and protect your personal devices from being compromised. The convenience that new technology brings also means that it can be easier to hack in some ways. However, these products are all easy enough to use that even those of us without Computer Science degrees can stay on top of our Bluetooth security. Guaranteeing your safety online only takes a few steps, and using a good proxy is the perfect way to make sure your personal information stays safe.
The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.