What Is An HTTP Proxy? (The Best Proxies For Web Scraping)
The Internet has been an essential part of society’s day-to-day reality for such a long time that it’s become second-nature to most people. It’s turned into such a quotidian element in our everyday activities that you probably hardly ever question how it works any more.
Yet, it’s a fact that with an ever-expanding source of information in the palm of your hand comes great power — and even greater responsibility. Learning the best practices for navigating the web and gathering data from it safely is a must. That’s where proxies and proxy servers come in.
More and more people, especially in enterprise environments, are using proxies to mask their identities online and gain an extra layer of security while they perform all kinds of duties. Proxies have also become popular among members of the general public who want to circumvent geolocation restrictions to go shopping or even make some money. Yet, despite the popularity surge, some users still get some basic proxy concepts all mixed up.
For example, it’s not unusual to hear terms like proxy, proxy IP address, and proxy server being used interchangeably, even by people who have been using these tools for years. Additionally, some users still have a hard time differentiating the numerous types of proxies there are and what they’re for. Knowing your proxies is key to choosing the right one for your business needs and making the most out of what these internet usage staples can do for you.
But we all have to start somewhere. Even those who now call themselves proxy experts once asked themselves, “What is an HTTP proxy?” If you came here with that same question, this post will help you better understand all there is to know about the subject matter. Feel free to use the table of contents below to skip to the parts that interest you the most.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

Proxies vs. Proxy Servers: What’s the Difference?

To understand what an HTTP proxy is, let’s first iron out some concepts that often get mixed up. Every Internet-connected device is represented by a unique combination of numbers and letters that provides identification and general location addressing when surfing the web. In computer networking, that’s what’s known as an Internet Protocol Address — or IP address, for short.
It’s important to note, however, that IP addresses are not tied to a particular device, but the connection between your machine and the Internet. In other words, the same device can have different IP addresses depending on where you’re connecting to the web and who your provider is. This means that when you use your laptop at work, you have a completely different IP address than you do when you use it at home or at your local coffee shop.
Your IP address is typically assigned by an Internet Service Provider — that is, of course, unless you buy one, but more on that later. They allow you to receive and send data online while letting the websites you browse identify where your requests are coming from.
This information could ultimately help some sites block you from accessing their content based on your location or whether you’re incurring suspicious activity. Normally, you wouldn’t need to hide your IP address when exploring the web, but there are some cases where you may want to. That’s when getting yourself a proxy might be of help.
What is a proxy server, and how is it different from a proxy IP address?
As you may know, a proxy is some kind of gateway that passes requests between your preferred device and a network. Yet, when we refer to proxies, we’re typically talking about proxy IP addresses, which are IPs you can get online from a proxy provider.
A proxy lets you go online under an IP address that’s different from yours. But, “Where do these intermediary IP addresses come from?” you may ask. This question leads us to the last concept you need to familiarize yourself with before moving forward with this guide: proxy servers.
A proxy server is, essentially, a computer on the internet with its own IP address. It acts as a middleman between your browser and the World Wide Web. Whenever you submit a web request online, it goes to the proxy server first. Then, the proxy server makes that web request for you (by proxy), fetches the response from the web server, and forwards the pertinent data back to you.
These physical or virtual machines hold numerous proxy IP addresses, so, in simple terms, they’re your source of internet connection IDs for your device. Besides changing your IP address so that the web server doesn’t know where your requests are coming from, a proxy server can encrypt your data to make it unreadable in transit, or block access to certain web pages, based on the IP address.
Proxy servers can be forward or reverse, which basically means they can sit on the client (you) or the server side. Forward proxy servers evaluate outbound requests from your computer and take action before sending it to the external resource. Reverse proxies, on the other hand, are those between a network and multiple internal resources. They allow large sites, for example, to balance loads and proxy traffic to individual servers.
Proxy server use cases
Most regular internet users won’t ever have the need to purchase an entire proxy server. Yet, buying one proxy IP address — or multiple, preferably — is rather helpful when performing a wide array of tasks online, including:
- Scraping the web
- SEO monitoring
- Accessing geo-restricted content
- Social media monitoring
- Ad verification
- Gaming
- Browsing anonymously
Proxy servers offer an excellent way to guarantee security, privacy, and online anonymity by rerouting your online requests. They can provide you with various IP numbers so that you can further hide your identity and conduct your internet-related activities with extra peace of mind. There are many different types of proxy servers to meet diverse client needs. HTTPS proxies are just one example.
HTTP Explained

The Hypertext Transfer Protocol — or HTTP, for short — allows files to be transferred between servers and clients all over the web. It was designed in the 1990s, and it’s paved the road for all sorts of data exchange online. This protocol has widely evolved and extended over the years, to the point that it’s nearly impossible to picture the Internet without it.
If it wasn’t for HTTP, you probably wouldn’t be able to send and display images, video, or sound online. This stateless and connectionless protocol is currently available in different versions:
- HTTP/1.0
- HTTP/1.1
- HTTP/2
- HTTP/3
While the older version of HTTP requires separate connections to communicate each time, the most recent variant can reuse a connection multiple times. Nowadays, HTTP/2 is used by almost 50% of all websites available, while the newer and lesser-known HTTP/3 is used by only 22%.
HTTP vs. HTTPS
From its origins in the ‘90s and until the mid-2010s, HTTP was the protocol of choice for numerous Internet sites. It wasn’t until 2014, when certain search engines recommended that all websites should switch to HTTPS, that this protocol started losing popularity to its more secure counterpart.
Search engines were so serious about this shift, that it offered a ranking bump to encourage users to take the plunge and ditch HTTP altogether. But why did HTTPS cause such a stir, and perhaps most importantly, what’s the difference between these sibling protocols?
For starters, HTTP has no data encryption implemented. It uses a basic type of hypertext transfer protocol — the same created in the ‘90s when the Internet wasn’t as complex. This application-level protocol is mainly focused on presenting information but not so much on how it travels from one place to another. This means all data transferred by HTTP could potentially be intercepted and manipulated, rendering users vulnerable to attacks.
Advantages of HTTP:
- It can be implemented with other protocols on the Internet
- It can be used on different networks
- Its pages are stored on computer and internet caches
- It’s platform-independent
- It allows cross-platform porting
- It doesn’t need runtime support
- It’s usable over Firewalls
- It makes global applications possible
- It needs no network overhead to create and maintain session state
Limitations of HTTP:
- It causes some privacy concerns as anyone can see the transferred content
- It has significant data integrity issues
- Malicious actors could easily alter the content
- It’s an insecure method for web browsing and data transferring
- It uses no encryption methods
What is HTTPS?
While both HTTP and HTTPS are essentially the same, the latter enables encrypted connections. It is more advanced than its predecessor, and also more secure, which is what the S stands for. HTTPS’s security features are powered by Transport Layer Security (TLS), which is the standard protection technology to build encrypted connections between clients and servers.
Without this protocol, any sensitive information you entered into a particular site would be sent plaintext. This would make it vulnerable to eavesdropping or interception by malicious actors. TLS also helps authenticate servers to further protect your data.
Using the HTTPS protocol is actually a requirement for all sites collecting payment information per the Payment Card Industry Data Security Standard. However, there are numerous advantages of using HTTPS for web navigation besides the added security. This protocol can also help sites with their SEO strategy, thus increasing page visibility. In addition, some browsers, are pushing for an HTTP-free web. That’s why they’re implementing measures to mark all HTTP sites as non-secure.
Advantages of HTTPS:
- Many sites running over HTTPS have a redirect in place to avoid running on HTTP
- It enables secure e-commerce practices and transactions
- It’s safe for online banking
- It’s protected by SSL technology
Limitations of HTTPS:
- It cannot secure cached confidential information
- SSL data can be encrypted only while being transmitted on the network
- It can’t clear the information in the browser memory
- It can increase computational overhead
With the increasing demand by the general public for a more secure online environment, the transition between HTTP and HTTPS is imminent.
Key differences between HTTP and HTTPS:
- HTTP doesn’t have a data encryption mechanism in place, while HTTPS provides SSL or TLS digital certificates.
- HTTP runs at the application layer while HTTPS runs at the transport layer.
- HTTP operates on port 80 by default; HTTPS runs on port 443.
- HTTP transfers plaintext data while HTTPS uses ciphertext.
- HTTP runs faster than HTTPS, as it doesn’t consume additional resources to encrypt the communication channel.
What Is an HTTP Proxy Server?

You’ve probably wondered at some point whether you’re safe while browsing the web. Even though it’s probably one of the most wonderful and useful inventions in the history of humankind (so far), it’s no secret that the internet has many dangers and challenges in store. Being cautious when navigating is non-negotiable these days. Luckily, proxies are a handy tool to increase online security.
As mentioned above, HTTP is used for sending and displaying all kinds of files across the web. Implementing this protocol to proxies is only logical. It helps strain all transmitted content. Essentially, HTTP proxies are high-quality content filters. They scan client-server communications to detect malware, spyware, or other types of cyberattacks. This kind of proxy can be used both by clients like you or web servers, like the ones used by the sites you frequent.
Through caching and web traffic compression, HTTP Proxy servers can help you save a lot of bandwidth. If your company needs to access huge, ad-heavy sites, an HTTP proxy can help you minimize the number of ads that reach your devices. This proxy option lets numerous users take advantage of the same connection at once, which becomes incredibly handy if your business has numerous workers.
HTTP proxies help business owners and managers increase their data security by allowing them to stop third parties from storing unauthorized files. These types of proxies can restrict network access much as a firewall would. In fact, they’re great for testing these popular network security systems.
Most common uses of HTTP proxies in business
HTTP proxies are an excellent alternative for enterprise-level users. They allow you to:
- Block particular content from reaching your network
- Block incoming connections
- Restrict access to certain URLs
- Allow or block some cookies
- Enable devices with no IP address or those in a private network to access the internet
- Cache data
- Reduce network loads
- Increase connection speed
- Freeing up bandwidth
HTTP-client proxies and HTTP-server proxies have the ability to sort out the content reaching them. Because of this, they can help you place restrictions on unauthorized files and prevent them from being stored on your devices to prevent attacks and other issues.You can set up your HTTP proxies to analyze HTTP and HTTPS headers, which are sections with data packets that give you a sneak peek of the content’s characteristics. This will help you determine the source of the content and ensure you can detect untrustworthy sources on time.
By acting as a firewall, it can further help you protect your network and devices. HTTP proxies can analyze the protocol and detect any anomalies based on a set of rules that dictate what normal is, including requests for comments (RFC) specifications. An anomaly example is a web server sending requests instead of accepting them or extremely long headers.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

Pros and cons of HTTP Proxies
HTTP proxies need to be configured by the user before being able to fulfill their functions. While that can be seen as a drawback for users who might not be as tech-savvy, it also allows for major customization. Some other advantages of HTTPS proxies are their ability to:
- Speed up web connections
- Maintain user anonymity
- Bypass internet restrictions
- Make external server requests
- Support multiple connections without impacting speed
Although HTTP proxies offer numerous convenient solutions, they also have some shortcomings, like:
- Not being able to encrypt connections
- Requiring technical background
- Lacking a centralized configuration when used by multiple people at a time
- Not providing access to other communication protocols
How does an HTTP proxy work?
The digital era is plagued with cybercriminals who pose a constant threat to individuals and businesses online. HTTP proxy servers filter out any suspicious activity over a particular connection. They can quickly block any potential attack from a foreign network, as they’re constantly examining traffic and fishing for malware. Among other things, these proxies can analyze the web traffic source before sending it to a client to ensure harmful content doesn’t reach the client network. HTTP proxies can be customized based on your business requirements.
HTTP proxies use a two-way communication method that lets them access the Secure Sockets Layer (SSL). This feature also enables them to reach HTTPS websites, even though they’re not based on the HTTP protocol.
When you incorporate an HTTP proxy policy into your machine’s configuration, you gain access to two different proxy actions which you can customize to meet your organization’s needs:
- HTTP-Client — You can configure this proxy action to give your network extensive protection from the content you and your employees (or other trusted users) download from the web. It protects your devices and network by filtering content and only allowing authorized files to be downloaded.
- HTTP-Server — This proxy action is typically configured by default to let most HTTP connections sent by clients pass through your public server. However, you can use it to prevent any malicious efforts to add or delete files from your server.
How to configure HTTP proxy settings
When you purchase a new proxy, you first need to set it up in your browser. In order to complete the process, you need to know the basics about ports — which are virtual locations inside your machine that require a number to be accessed. When you give your brand new proxy a certain port number, this means you’re allowing it to enter that virtual location to do what you want it to do.
HTTP protocols typically use specific ports within your computer by default. For HTTP, for example, these ports are 80, 8080, and 3128. If you’ve been having trouble using your HTTP proxies to cache downloaded files and increase the speed of HTTP proxy website downloads while exploring your targeted sites, it might be because you’re not using the right ports. You might want to give the ones mentioned earlier a go.
Once you understand how to find your port for HTTP and HTTPS proxies, you can go ahead and set them up. Your provider will typically give you step-by-step instructions, but it’s often as simple as going to your settings and pasting the new IPs into the proxy field. You can also easily turn them off when you want to surf the web with your default IP. In this case, you’d simply need to go to the settings and restore the proxy settings.
Finally, you’ll want to enable your proxy through your provider to get it up and running in your network. This will prevent non-authorized users from getting online using your HTTP proxies and keep your data safe. To set this up you’ll need to:
- Log into your proxy account
- Go to the dashboard
- Find the authorization type you’d like to use
- Enter your proxy IP address
- Click “Add IP”
Why Implement an HTTP Proxy in Large Scale Projects?

HTTP proxies follow pretty much the same operating principles as other types of proxy servers. Typically, all proxies alter web requests by masking the original IP address that made them and assigning a new one.
HTTP proxies can also modify the content sent by the servers, depending on which side they’re implemented on during the data transferring process. Businesses can set up their own goals and configuration to use their HTTP proxy for:
Security — which allows you to set anomaly detection rules that let you recognize and deny suspicious packets. HTTP proxies let you protect your server from external network attacks. Using HTTP proxies will help you prevent data breaches and keep malicious actors away from your businesses’ sensitive information.
By keeping your data secure, you’ll maintain your reputation among your customers and prove you can keep their information safe. The additional security layer HTTP proxies offer your organization will also give you peace of mind as your employees conduct their daily tasks.
Productivity — not only will stopping your employees from entering certain sites keep your network safe, but it will prevent distractions and keep everyone in the zone while working. Your HTTP proxies will let you ensure nobody in the office visits off-limits sites or platforms that are not relevant to their duties.
Network traffic balance — This can help you prevent server crashes that could cost you time and money. HTTP proxies are an excellent tool to ensure your system runs smoothly and with no overload for a seamless experience while browsing or scraping the web.
Faster connections — Proxies can help you compress traffic and cache files. This will let you and your teams navigate much faster and finish work in no time. Proxies are a great way in which companies like you boost efficiency within their departments.
HTTP proxies and web scraping
If you’ve been scraping the web for a while now, you may know the importance this activity has in business. It allows you to monitor customer behavior, market trends, competitors, performance, and SEO. Yet, as useful as collecting relevant information from the Internet is for entrepreneurs and data researchers, it’s heavily frowned upon by website admins, who tend to turn to anti-bot technologies to protect their data and their sites from crawlers and spiders.
To collect the data you need quickly, you would need to send thousands of requests per second to a site. Needless to say, this looks nothing like regular user behavior, and it would immediately give you away. In consequence, the site you’re extracting data from could ban your IP addresses to stop you right on your tracks. Although often temporary, an IP ban could significantly limit your research and make you waste valuable time.
There are numerous measures you can take to avoid getting caught web scraping. One of them is using the right proxies. By diversifying your IPs, you can make the web interactions your bots make for you look much more natural. This will keep web servers happy, thinking it’s a person — not a robot — who’s collecting data from their site. Before you know it, you could have all the information you need to help your SEO strategy, user sentiment, and competitive data analysis, and more without raising any red flags.
Web scraping with HTTPS proxies is a lot more effective and time-efficient than trying to collect all the information you need manually, which could lead to multiple human errors that could potentially render your research useless. Moreover, using proxies to make multiple requests in a short period will allow you to focus on other important business matters. A proxy server can provide you with a large collection of IP addresses to overcome bans and gather all the data you need seamlessly.
A myriad of businesses and corporations gravitate around HTTP proxies for a few excellent reasons. HTTP proxies provide them with a way to keep their scraping exercises much more secure. They also allow them to identify all content that could lead to data breaches and eliminate it to avoid further complications. However you look at it, HTTP proxies have certainly proven to be a powerful tool for finding and retrieving valuable information and keeping tabs on your customers and competitors.
How HTTP Proxies Differ from Other Proxies

Unlike some other popular types of proxies like SOCKS, HTTP proxies are designed primarily for crawling and scraping the web. With these proxies, you can easily collect data from search engines, e-commerce sites, social media platforms, and many other kinds of online sites.
That’s because HTTP and HTTPS proxies allow you to interpret the data before extracting and downloading it. As mentioned above, they let you filter through all available data and save only what’s relevant to you, which helps save time and resources.
HTTP proxies vs. SOCKS proxies
Much like HTTP and HTTPS, SOCKS is yet another internet protocol. SOCKS is typically used for traffic-intensive tasks — think content streaming or peer-to-peer sharing. It stands for Socket Secure and uses TCP connections to send and receive datasets across the web.
SOCKS proxies work much like any other proxy type. They hide your IP address and establish server connections on your behalf. Yet, unlike HTTP proxies, SOCKS cannot interpret web data. It merely facilitates communication between your browser and websites with a firewall. SOCKS proxies work on network protocol type on any port. HTTP proxies are recommended for business owners that need a high level of customization to cover numerous goals and use cases, like web scraping. They provide users like you with:
- A higher scraping success rate — By allowing you to configure HTTP request headers, HTTP proxies can help you facilitate access to restricted targets. This will lower the risk of getting blocklisted by the site you’re trying to scrape.
- Added security — HTTP proxies allow you to detect and deny suspicious data packets like malformed content, spyware, or ransomware trying to enter your server. That’s why they offer a higher level of security when performing your web scraping activities.
- Clean data — HTTP proxies have the ability to understand the data that passes through them while acting as a middleman between clients and servers. In other words, an HTTP proxy can be configured for caching web data and content filtering to help you expedite your exercise. When using HTTP proxies, you’re able to avoid collecting unnecessary data.
- Bandwidth savings and improved speeds — A good HTTP proxy server can offer you better overall network performance. That’s because they can save a local copy of the websites you visit. This way, when you visit the sites you want to extract data from, your proxy will look for the most recent copy of the site and send you to the saved copy. Moreover, if multiple people send requests for the same site from the same proxy server at once, the proxy server will send it as if it was one HTTP proxy request, thus saving bandwidth and increasing browsing speeds.
SOCKS proxies can be used in multiple applications and scenarios as well. However, unlike HTTP proxies, they’re compatible with any port or network protocol. By using TCP, they don’t need to rely solely on establishing HTTP connections. These types of proxies can also take advantage of User Datagram Protocol (UDP) to ensure efficient performance by delivering datagrams over a network.
As mentioned previously, SOCKS proxies are a great choice for use cases that involve dealing with firewalls. That’s because firewalls can prevent users from initiating arbitrary TCP connections to outside servers, and SOCKS can make it happen. HTTP proxies can do this too, but they’re limited to sites with an HTTP connection.
Risks of Not Using the Right HTTP Proxy Services

Choosing the right proxy server is fundamental and should not be taken lightly. Failing to do so could compromise your network’s security and your device integrity.
Using a free proxy service is not as good an idea as it may seem. It’s true you may be saving the initial cost of purchasing the proxies you need. However, getting your data exposed to malicious actors could potentially cost you hundreds — or even thousands. Obtaining free proxies online from nearly any provider is a risky practice. This is like tossing a coin and hoping for the best, but you could be endangering your data and your customers’ data for no reason. Getting your reputation ruined is a hefty price to pay.
Free proxies usually don’t invest in backend hardware or encryption. It’s important to know proxy servers with no encryption are pretty much useless when it comes to privacy and security. Anyone listening could pull your information, passwords, and other sensitive information easily if your requests are being sent in plain text. Besides, if you see performance issues or any other problems, free proxy providers will rarely have adequate customer support. What’s more, dubious free proxy server services may just be looking to steal your credit card information.
Keep in mind your proxy server has access to your original IP address and web request information. That’s why you need to ensure your provider won’t log and save your information. Proxy server services that do this won’t do much to protect your privacy. Conversely, they’ll be jeopardizing it by sharing it with third parties.
Finding a Suitable HTTP Proxy Solution

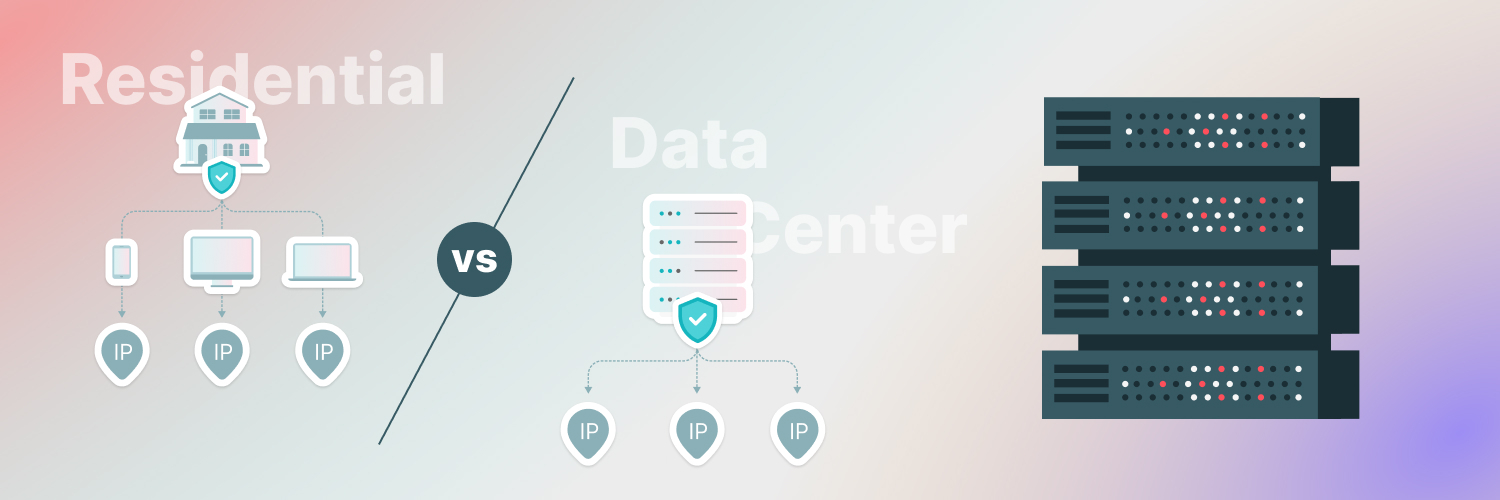
Finding the right proxy solution for your business needs is essential to achieving your business goals. As mentioned above, proxies are not a one-size-fits-all solution and there are many types for various purposes. Selecting the most suitable proxy for you can get a bit overwhelming. If you’re web scraping, however, you should keep your focus on data center and residential proxies.
Residential proxies
Residential proxies are a great way to play it safe while engaging in scraping activity. They look just like regular IP addresses assigned by an Internet Service Provider — because they are. This type of proxies come from actual users that agree to let their IP addresses be used as a node in a network.
In consequence, web servers are less likely to detect them and ban them. Using rotating residential proxies will nearly guarantee you won’t get your IP banned or have other setbacks crawling your favorite sites. Visit our site and learn more about the best ethically sourced residential proxies available.
Data center proxies
Data center proxies are a more affordable option. They don’t come from your average Internet Service Provider. Instead, they’re created in a data center, as the name states. This makes it easier for you to purchase them in bulk so that you can rotate them as needed. However, by not being sourced from real users, they’re more easily detectable. On the bright side, data center proxies are a lot faster than their counterparts.
Rayobyte sells both data center and residential HTTP(S) proxies to help you filter out the content you don’t want and expedite your web scraping exercise. We’re committed to giving you peace of mind and fulfilling your data extraction activities. Our proxies will let you optimize your network for crawling and scraping. Additionally, they will help you increase your team’s productivity and reduce the risk of security breaches. If you need an effective solution for your web scraping needs, inquire about our data center proxies and get started today.
Buy HTTP Proxy Services With Us!

You can never be too cautious when surfing the web. The abundance of cybercriminals and other malicious actors that exist on the Internet can jeopardize your information. Using the right proxies is an excellent way to reduce your network’s vulnerabilities and protect your privacy. It will let you and your employees surf the web anonymously and more securely. There are many types of proxies available, but having your business goals clear will help you choose the one that best fits your needs.
With a unique set of features that improve network security while allowing you to extract high volumes of data quickly, HTTP proxies are an excellent business solution that pays off. They’re the best type of proxy currently available to scrape the web. Not only will using HTTP proxies save you tons of time, but it will also free up your disk space. Getting an HTTP proxy from a trustworthy provider online is your best bet if you want to improve your company’s security features and connection speed while gathering the data you need.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.