Semi-Dedicated Data Center Proxies Quick Start Guide
The internet provides a wide ocean of information and possibilities. However, geographical restrictions, website limitations, and the need for anonymity can all impede our capacity to freely browse.
Proxy servers act as intermediates between your device and the internet, providing an additional layer of protection and control. Semi-dedicated data center proxies, in particular, strike a mix between affordability and functionality, making them an effective tool for a variety of online operations.
This article digs into the world of semi-dedicated data center proxies, teaching you how to properly use their capabilities. We’ll look at what they are, their benefits and drawbacks, how they differ from other proxy kinds, and, most importantly, how to start utilizing them.
What Are Semi-Dedicated Data Center Proxies?

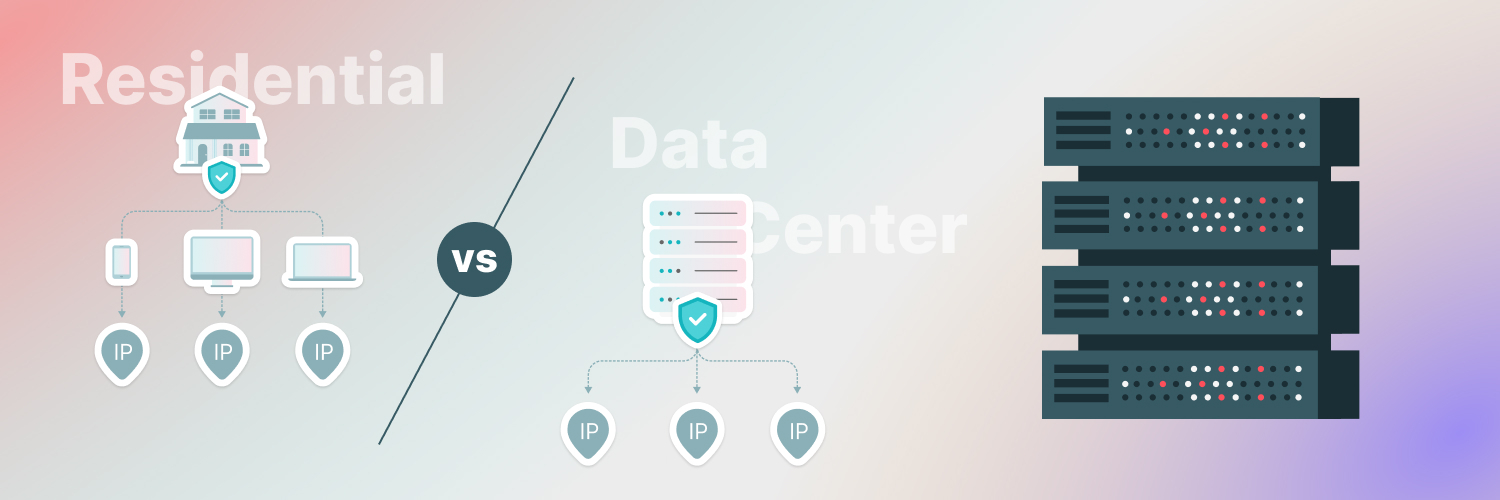
Semi-dedicated data center proxies are proxy servers that fall somewhere between shared and dedicated. Unlike shared proxies, which share a single IP address with several users, semi-dedicated proxies give a collection of IP addresses for a smaller group of users. This improves performance, reliability, and privacy over shared proxies while remaining more cost-effective than dedicated proxies.
How Does Semi-Dedicated Proxy Work?

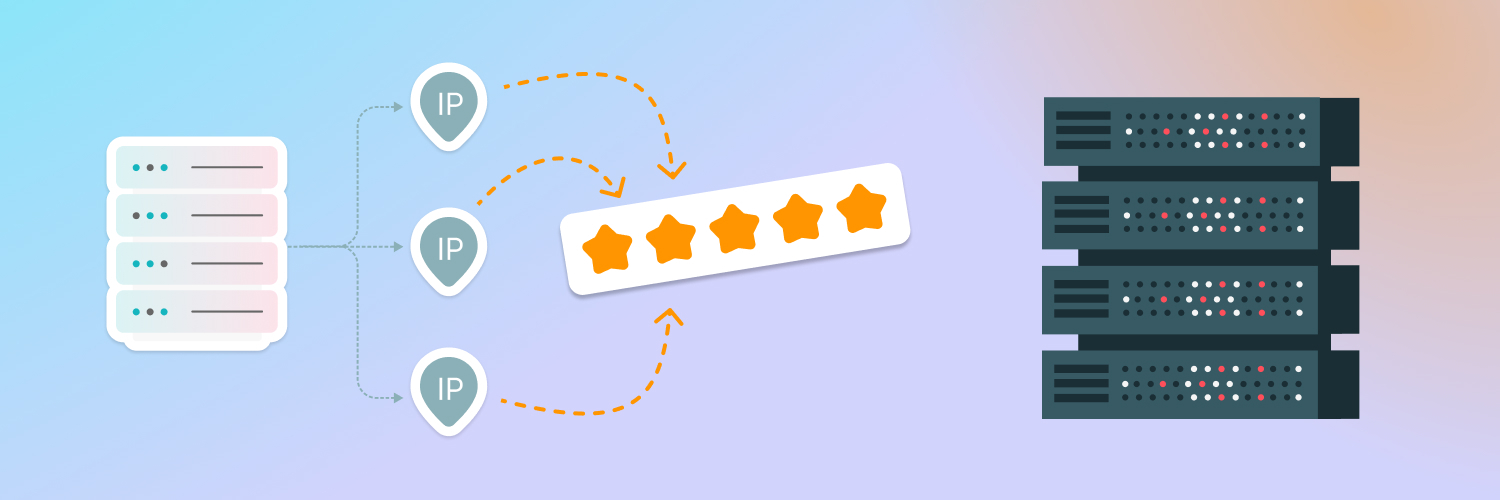
According to a study done by tech.org, semi-dedicated proxies operate by connecting to a global network of data centers using IP addresses. There is a restricted user-to-IP ratio since certain IPs are configured to handle traffic from a specific set of users.
Each user is given one to ten IP addresses to use from their pool. As a result, such IPs provide you with a specific fraction of their bandwidth and resources. However, the IP addresses may be shared with a small group of other users.
When a client connected to the semi-dedicated proxy attempts to access an internet resource, the request is first sent to the proxy server. Once the client’s IP address has been replaced with its own, the semi-dedicated proxy server processes the request and sends it to the intended internet server.
Because fewer individuals use each IP, consumers are assured a certain amount of bandwidth and resources from each semi-dedicated proxy IP. This avoids the congestion problems that often affect shared proxies.
Most semi-dedicated proxy services allocate IP addresses dynamically. This means that you will be issued a different IP address each time. When you request a proxy, you are assigned an available IP address from the pool. This improves the availability of IPs for all users.
Use Cases For Semi-Dedicated Proxies

Here are some of the most common scenarios where semi-dedicated proxies are an excellent fit:
Web Scraping And Data Extraction
Web scrapers and data extraction applications commonly use semi-dedicated proxies to gain access to websites and online resources while retaining privacy and dependability. The smaller user pool and dedicated IP addresses can help you avoid IP-based limitations and reduce the likelihood of being blocked or blacklisted by target websites.
Online Advertising And Marketing
Businesses that engage in online advertising, such as affiliate marketing, display advertising, or social media marketing, might utilize semi-dedicated proxies to rotate their IP addresses and avoid any complications with IP-based ad verification or targeting.
Content Delivery And Caching
Content delivery networks (CDNs) and caching services can use semi-dedicated proxies to distribute content from several locations, increasing performance and lowering the danger of IP-based restrictions.
Seo And Competitive Intelligence
Semi-dedicated proxies allow digital marketers and SEO specialists to obtain competition data, watch keyword ranks, and monitor online reputation without the risk of IP-based difficulties.
Social Media Management
Semi-dedicated proxies can be used by agencies as well as individuals who manage many social media accounts to rotate IP addresses and evade account limits or bans.
Financial Trading And Market Research
Financial professionals, such as traders and market researchers, can use semi-dedicated proxies to gain access to financial data and trading platforms while retaining their privacy and trustworthiness.
Personal Privacy And Security
Individual users can also benefit from semi-dedicated proxies to improve their online privacy and security, especially when dealing with sensitive information or using public Wi-Fi networks.
Leveraging Semi-Dedicated Proxies For Business

For small businesses seeking to leverage proxy services without incurring large costs, semi-dedicated proxies present an ideal solution. These proxies offer a middle ground, providing more features than free shared proxies and costing less than dedicated proxies.
Semi-dedicated proxies are particularly suited for smaller-scale projects, allowing businesses to access advanced proxy functionalities such as enhanced security and the ability to navigate geo-restricted content, all while maintaining a cost-effective budget.
Consider semi-dedicated proxies as an opportunity to assess the value of proxy services. This cost-effective approach allows enterprises to test and use proxy functionality without the financial commitment necessary for specialized solutions.
However, it is vital to note that semi-dedicated proxies may not be sufficient for operations requiring extensive data extraction. Such demanding tasks require the usage of dedicated proxies, which provide greater resources, speed, and performance while providing complete control and efficiency for your business requirements.
Benefits Of Semi-Dedicated Proxies
We’ve established that semi-dedicated proxies offer a balance between shared and dedicated options. But what makes them truly shine? Let’s delve into the key advantages that set them apart:
Improved performance
Compared to shared proxies, semi-dedicated proxies can provide quicker connection speeds and lower latency because fewer users are sharing the same IP addresses.
Enhanced Privacy
The possibility of IP address blacklisting and other problems related to shared proxies is decreased by the smaller user pool and dedicated IP addresses.
Increased Reliability
Semi-dedicated proxies are more resilient to outages and downtime since the failure of a single IP address within the pool has no impact on the proxy service’s overall availability.
Cost-effectiveness
Semi-dedicated proxies are less expensive than dedicated proxies, which give you a single IP address for your exclusive usage, but they still offer better privacy and performance.
Unlocking Global Content
Semi-dedicated proxies enable the routing of internet traffic through servers in many countries and cities. This feature allows users to get around geographical content limitations by imitating internet activity from different locales.
Scalability
As your requirements evolve, you can easily upgrade to a dedicated proxy or expand your semi-dedicated proxy solution to accommodate more users.
Support HTTP and SOCKS protocols
Semi-dedicated data center proxies provide HTTP and SOCKS proxy protocol functionality.
HTTP proxies enable anonymity, content unblocking, and improved web scraping, but SOCKS proxies give interoperability with a broader range of apps and increased security through traffic encryption.
This versatility enables customers to select the best protocol for their needs while smoothly integrating the proxy with a variety of online resources and services.
Challenges of Using Semi-Dedicated Proxies

While semi-dedicated data center proxies have several advantages, there are certain potential drawbacks that users should be aware of. For instance:
Shared infrastructure limitations
The shared nature of semi-dedicated proxies can result in several limitations. Because numerous users are using the same IP address, the available bandwidth and resources may be shared, potentially resulting in slower connection speeds or performance concerns, particularly during peak usage times.
Strategies to address shared infrastructure limitations
- Monitor your proxy consumption and performance closely to find bottlenecks or slowdowns.
- Communicate with your proxy provider to learn about shared infrastructure capabilities and explore choices for switching to a dedicated proxy or scaling your semi-dedicated arrangement if necessary.
- Optimize your online surfing and scraping operations to reduce resource usage and make better use of the shared proxy.
Potential IP Address Conflicts
When using a semi-dedicated proxy, IP address conflicts are possible, which occur when numerous users attempt to access the same website or service at the same time using the same IP address. This can result in issues like account suspensions, human verification challenges, or even IP address bans.
Strategies to address IP Address conflicts
- Coordination with other users (if any) is necessary to avoid visiting the same websites or services at the same time.
- Use proxy rotation options, if available, to automatically cycle through multiple IP addresses to avoid conflicts.
- Maintain contact with your proxy provider and report any ongoing IP address-related concerns for their assistance.
Limited Customization and control
Semi-dedicated proxies may provide less flexibility and control over the proxy architecture than dedicated proxies. Users may have restricted access to advanced options or the opportunity to customize the proxy configuration to meet their requirements.
Strategies to address limited customization and control
- Conduct extensive research and choose a proxy service that provides the required level of flexibility and control, even if it means paying a little higher price for a dedicated proxy solution.
- Communicate with your proxy provider to learn about the available customization options and work with them to tailor the proxy setup to your needs.
- If you have the technical ability and resources to maintain a more customized proxy system, consider using self-hosted proxies or virtual private servers (VPS).
Potential security and privacy concerns
In a semi-dedicated proxy arrangement, numerous users use the same IP address, which may raise security and privacy problems. Activities of one user may have an influence or be visible to other users on the same proxy.
Strategies to Address Security and Privacy Concerns
- Ensure that your proxy service employs strong security measures, such as encryption, tight access controls, and logging standards.
- To improve your online privacy and protection, install additional security layers like a virtual private network (VPN) or a secure browser extension.
- Educate yourself on the best ways to ensure online security and privacy when using a shared proxy environment.
Setting Up Semi-Dedicated Proxies

To get started with semi-dedicated data center proxies, follow these steps:
1. Choose a reliable provider
Research and choose a trusted proxy service company that provides semi-dedicated proxies. Look for characteristics like fast connections, strong security, and responsive customer service.
2. Sign up and create an account:
Visit the provider’s website to sign up for a semi-dedicated proxy plan. Follow the steps to create your account and finish the setup procedure.
3. Obtain your proxy details:
Once your account has been created, you will be given the information you need to connect to your semi-dedicated proxy, including the server address, port, and login credentials.
4. Configure your proxy settings
Depending on the device or software you’re using, the procedures to configure your proxy settings may differ. However, the general process often includes the following:
- For web browsers, navigate to your browser’s settings and discover the proxy configuration options. Enter the server address, port number, and login information provided by your proxy provider.
- For desktop apps, navigate to the application’s network or proxy settings and enter the necessary information.
- For mobile devices, go to your device’s settings, find the network or Wi-Fi settings, and enter the proxy information.
5. Test your proxy connection
After you’ve configured your proxy settings, verify the connection to check it works properly. You can use online tools or visit websites to verify your IP address and location to ensure that the proxy is working properly.
Maximizing the Benefits of Semi-Dedicated Proxies

Once you have your semi-dedicated proxies set up, here are some tips to help you get the most out of this powerful tool:
Understand Proxy Rotation
Some proxy providers allow you to automatically rotate your IP address, which can be useful for tasks like web scraping or evading geo-restrictions. Familiarize yourself with this feature and how to use it efficiently.
Optimize for Web Scraping
Semi-dedicated proxies might be very handy when scraping less popular domains. Experiment with various proxy configurations and session management strategies to improve scraping efficiency while avoiding detection.
Use Multiple Proxies
If you need more than three concurrent users, consider expanding your semi-dedicated proxy arrangement by adding more proxies or switching to a dedicated solution.
Monitor Performance
Keep track of your semi-dedicated proxies’ performance, including connection speeds, dependability, and any difficulties that may develop. Communicate with your provider to address any concerns and maintain peak performance.
Prioritize Security
While semi-dedicated proxies can give some privacy, it’s critical to follow good security measures like using strong passwords, enabling two-factor authentication, and monitoring your account for suspicious behavior.
Conclusion

Semi-dedicated data center proxies offer a cost-effective and flexible solution for individuals and small teams who need to shield their IP addresses, access geo-restricted content, or enhance their web scraping capabilities.
Remember, as with any online tool, it’s crucial to use semi-dedicated proxies responsibly and in compliance with applicable laws and regulations. By following the steps outlined in this quick start guide, you can easily set up and start leveraging the benefits of semi-dedicated proxies to unlock the full potential of the internet.
The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.