What Is A Proxy List And How Does It Work?
The internet contains a vast amount of data, and its contents are just waiting to be mined for actionable insights. But unless you plan to access those sites directly with your own IP address, you’ll need an intermediate way to connect. You’ll need a proxy list.
A proxy list is a compilation of IP addresses stored on varying proxy servers. It can give you multiple avenues to link up with the web. It’s essential for applications as diverse as market research, price collection, SEO monitoring, and especially web scraping — and many other use cases where your privacy must be protected. Proxy lists can be grouped according to several factors (public or private, protocol, geography, etc.), so identifying the right one for your project can be difficult.
Looking For Proxies?
Sticky, rotating, residential, data center… whatever you need, we’ve got it!

In this how-to-use proxy list guide, we’ll take a deep dive into how they work and how to use them for your project. We’ll also show you what kinds of proxy lists are available, along with their pros, cons, and drawbacks — and how Rayobyte can supply the right one for you.
What Is a Proxy List?

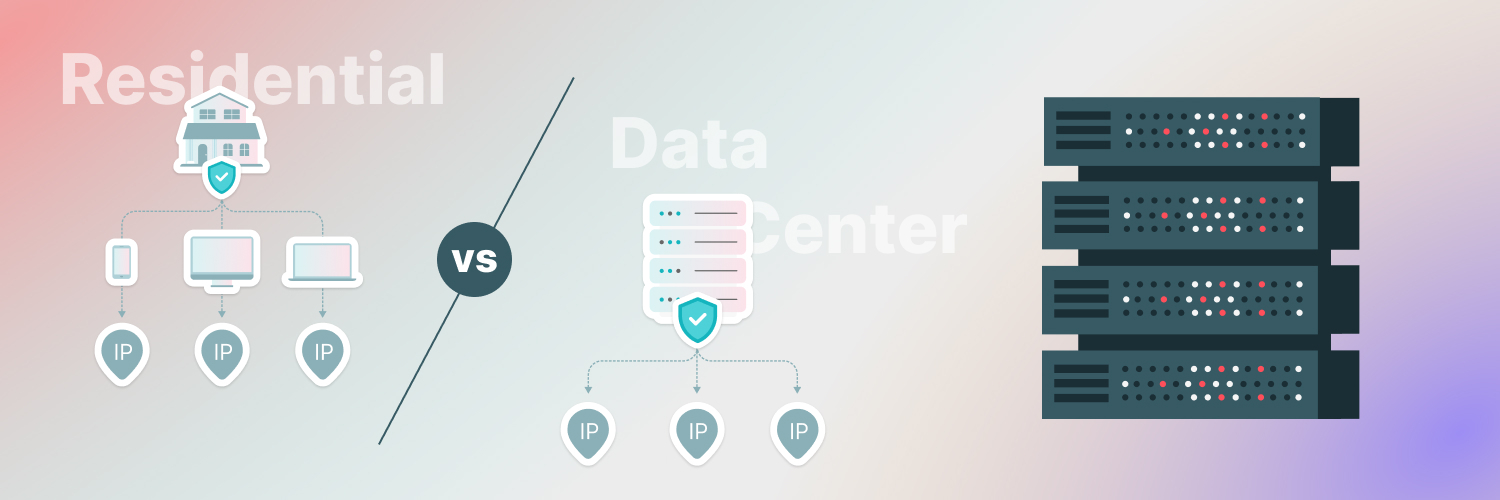
When you connect to the web, your IP address sends a request to the site to bring data back to you. Rather than use the IP address your network has supplied, you may prefer to keep your anonymity by routing the request through another IP address instead. These are web proxies, and the collection of alternate IP addresses (along with their ports) forms a web proxy list. Some common types of proxies include:
The definition is simple enough, but proxy lists can be very diverse. There are five main categories of proxy lists — free, open/public, closed, private, and fresh.
Proxy lists are also classified according to the information within their IP addresses, and other factors can impact their use. We’ll elaborate on each of these later, but some proxy list parameters to consider are:
- Protocol type (HTTP, HTTPS, SSL, SOCKS, SOCKS5, etc.)
- Geography (country or city)
- Anonymity (transparent, distorting, or elite)
- Proxy IP and port number (TCP and IP)
- Freshness (“virgin” or previously used)
- Bandwidth (limited or unlimited)
- Stickiness (static or rotating)
- Update frequency
- Support
Some of these factors pertain to the data found within the IP address, while others depend upon the proxy provider you use. That means you’ll need to consider not only the technical details but also the provider behind them — ethical sourcing is always a must.
What Are the Main Categories of Proxy Lists?

Once you know what to look for in a proxy list, you can decide which main category you’d prefer. As mentioned, the five main categories of proxy lists are: free, open (or public), closed, private, and fresh. While there is some overlap, several important differences could impact your choice. Most of these differences pertain to accessibility but can affect their safety level, privacy risk, and how far they can take you before you get blocked, so consider your choice carefully.
Open (public) proxy lists
Possibly the most common proxy list classification, open proxy lists are simply those available to the general public. With no vetting or monitoring measures, any user can go online and access these pools of IP addresses.
The advantage of open proxy lists is that they’re widely accessible, allowing anyone in need of a proxy to obtain an alternate IP address. They’re also typically free, making them an attractive option for users on a tight budget. Open proxy lists are often available in larger quantities than other proxy types, granting users access to enough IP addresses to scrape a vast number of sites.
Despite those advantages, open proxy lists have many drawbacks that make them a poor choice. First, because they’re not monitored, hackers and other bad actors may be just as likely to use them as legitimate proxy list customers. The IP address can be associated with a malicious threat or other problematic behavior and expose the user to a greater risk of viruses and other malware.
Another disadvantage of open proxy lists is that providers may bait customers into handing over their IP address, so users end up surrendering their digital privacy — the very thing they want to avoid. The IP addresses in open proxy lists are also relatively easy for a server to detect, increasing your likelihood of getting blocked or blacklisted from the websites you’re attempting to access.
Closed proxy lists
Unlike open proxy lists, closed proxy lists aren’t available to anyone. Closed proxy providers vet their users first to screen out any bad actors, making them a more secure option than their open counterparts. They do this by restricting access to only those users within a given subnet or geographical area or by requiring users know the address and password to use the server.
By structuring themselves as a pre-defined network, closed proxy list providers prevent malicious threats or nameless entities from using their servers. And because they’ve vetted each user and established a valid identity for each, they can tie any problems back to the source, ensuring greater security for the network.
While the proxies themselves function the same way, the monitoring that closed proxy providers do makes them more secure and improves their performance. Because they’re not bogged down with illegitimate or malicious actors, a closed proxy provider’s servers usually operate at a greater speed, offering users a faster experience. They also can deliver greater anonymity, though their membership fees mean they come at a price.
Free proxy lists
As their name implies, users can obtain free proxy lists at no cost. That may sound simple enough, but there’s a distinction between free proxy lists and open proxy lists. Both may be free, but free proxy lists can still be restricted in their access, while open proxies are not.
For example, businesses may furnish employees with free proxy lists to conduct their operations, or they may offer them to customers to market their services or collect data. They may still be free, but they’re only available to certain customers. That means almost all open proxy lists are free, but not all free proxy lists are open.
The advantage of free proxy lists is their cost-effectiveness, but as with open proxy lists, their disadvantages lie in their safety, privacy, and detection risks. Using free proxy lists can expose you to malware or viruses, potentially damaging your device. Free proxy providers can also collect activity logs or other personal information in exchange for their lists, which they could then use for their own research or sell to third parties — compromising your privacy again.
Another disadvantage of free proxy lists is their poor performance. The IP addresses obtained from a free proxy list generator are especially unreliable and are easy to detect. The servers containing free proxy lists frequently have more limited bandwidth, resulting in less speed until you upgrade — which is how they get you to subscribe.
Private proxy lists
Unlike open proxy lists, which are accessible to the public, the IP addresses found in private proxy lists are owned exclusively by the user. That means you won’t be logging on with an IP address that someone else is already using. Your IP address belongs to you and you alone.
One of the main benefits of a private proxy list is that it won’t be used for any purposes outside your own. That makes them more secure than other proxy list types, and since they often consist of residential proxies that better mimic human behavior, their IP addresses can be harder to block.
Looking For Proxies?
Sticky, rotating, residential, data center… whatever you need, we’ve got it!

Another advantage of private proxy lists is higher speeds, since you’re the only one using those addresses. Private proxy lists can also possess custom features that can assist users in their web scraping endeavors, such as originating from certain geographical locations to target geo-specific content or data. Other upsides of private proxy lists include:
- Larger quantity
- Unlimited traffic
- Greater anonymity
- Support for multiple protocols
- More frequent updates — often hourly
- Efficient caching
- Better customer support
Their exclusivity makes them more expensive than public proxy lists, but these advantages often make them a worthwhile investment.
Fresh proxy lists
Also known as “virgin” proxy lists, fresh proxy lists have never been used. This difference makes them highly prized among proxy communities, as their freshness makes them almost impossible to ban or block. Fresh proxy lists can be public or private, so the other benefits they provide will depend on which category they fall into.
What Information Is in a Proxy List?

Once you know the general categories, you can refine your proxy list search according to the desired information found within the list. This will allow you to select the proxies that best meet the technical requirements of your project, giving you the best chance for success. The information you’ll want to base your proxy list selection on may include IP address type, proxy IP and port number, geography, and anonymity, but other factors exist as well.
IP address type
IP addresses are based on two different internet protocols: IPv4 or IPv6. IPv4 (Internet Protocol Version 4) creates IP addresses from an 8-digit code separated by four periods, while IPv6 (Internet Protocol Version 6) employs a hexadecimal system and has vastly more possibilities than IPv4.
There are other reasons why knowing which IP address type you’re using is beneficial, but one of them is that it can help you tell if your proxies are fresh. Since all IPv4 addresses have been taken, fresh proxy lists will contain IPv6 addresses — though just because it’s an IPv6 proxy list doesn’t mean it’s fresh.
Proxy IP and port number
Devices use two network protocols to connect: the IP and TCP layers. The IP or network layer will show the actual IP address that you’re using to mask your own, while the TCP (Transmission Control Protocol) is the transport layer that maps out the ports you’re using to connect. Some common ports are:
- HTTP (25, 80, 8080)
- HTTPS (443)
- SSL (443)
- SOCKS (1080, 9000-1000)
- SOCKS5 (any port)
These port types have different security measures (more on that later), so if your project has specific security requirements, you may want to browse through your proxy list and select which port type the proxy employs.
Geography
Proxy lists will also state their IP address’ location, and can be grouped according to country or city. These proxies share a subnet, which organizes networks into more manageable pieces (like common geography) for better communication.
Having IP addresses from different locations is essential for some data collection or web scraping projects. Some website content is geo-specific and varies depending on the visitors’ location. Users may only be able to gain access to the data they seek if their IP address location is a match, so the ability to vary their location is a must.
Anonymity
The primary purpose of a proxy is maintaining your privacy while online, but some users may require a higher degree of privacy than others. Proxy lists display their IP address’s anonymity level so that users know how hidden they are.
There are three levels of anonymity. They are:
- Transparency (Level 3), which fails to completely cover the original IP address. It shows its own IP in the “via” header. This makes tracing possible, so they don’t protect your anonymity.
- Anonymous/distorting (Level 2), which covers up your source IP but still identifies itself as a proxy. This is the most common anonymity level.
- Elite (Level 1), which masks your source IP and changes the information in the “request/response” header. It also removes the “via” header, leaving no trace behind.
Elite proxies are favored for their high degree of anonymity, so consider them if your project demands the utmost privacy.
Uptime and latency
Proxy lists will also display uptime and latency (in ms), which will impact the speed of your web scraping project. Consider these if you need to do your scraping fast.
Protocol-Based Proxy Lists

Because their security procedures vary, proxy lists are often grouped according to the protocol they’re based on. The main protocol types are HTTP, HTTPS, SSL, SOCKS, and SOCKS5. If your project requires a certain security schematic, make sure you filter your proxy list selection to match.
HTTP proxy lists
The HyperText Transfer Protocol (HTTP) is connectionless, text-based, and retrieves data elements of all types from web pages. HTTP proxy lists are comprised of IP addresses that use the HTTP protocol, and since this is the most common type, there are more proxy lists of this variety than others. These IP addresses are the least secure, so users seeking greater security should use a different proxy list.
SSL proxy lists
Another protocol is the HyperText Transfer Protocol Secure (HTTPS). It functions in much the same way as HTTP, but it adds the Secure Sockets Layer (SSL) as an added means of protection.
SSL encrypts data while it’s in transit, making it impossible to read if intercepted. This gives users extra security and anonymity, as their identity won’t be discovered even if a breach is attempted. Modern browsers will also warn you about websites that don’t have an SSL certificate, letting you know if your proxy is at risk if you access the site.
An SSL proxy list provides IP addresses that employ the HTTPS protocol and are most often used when security is a higher priority. The most common applications include the financial sector or other industries where personal information must be entered.
SOCKS4/SOCKS5 proxy lists
Short for SOCKet Secure, the SOCKS protocol is another way to transmit data securely. It uses secure shell (SSH) tunneling to carry data across a firewall and is commonly used for high-traffic tasks such as content streaming or peer-to-peer (P2P) sharing. SOCKS5 is an updated version of SOCKS4, and supports encryption, multiple authentication methods (credentials and GSS-API), and the User Datagram Protocol (UDP).
A SOCKS5 proxy list contains IP addresses supported by the SOCKS5 protocol. These SOCKS5 proxies are ideal for establishing a connection for users seeking the security of a firewall (if they have no other way to connect). They’re also popular for high-speed applications such as torrenting and streaming.
Other Proxy List Types

While those are the main categories of proxy lists, other specialty types exist as well. Some of them are:
- Web proxy lists. Also known as Common Gateway Interface (CGI) proxies, web proxy lists function only with the use of a web browser and work by entering the target URL in an embedded form.
- Mirror proxy lists. A favorite among the torrenting community, these work by duplicating a site’s interface and design and then accessing it with a different URL. Though this practice is often associated with negative activity such as piracy, it can also be used for legitimate purposes such as software development or testing.
- Geography-based proxy lists. If you need to target geo-specific data, you may want to filter your proxy list according to the server’s location.
- Device-specific proxy lists. Some websites behave differently based on the device that accesses them. If users need to analyze content according to how it displays on certain devices — for web development purposes, for instance — they may need a proxy list that consists of only specific device types.
- Server-specific proxy lists. Rather than group them according to geography or functionality, it may be better to obtain a list of proxy servers or subnets and then group them accordingly.
Proxy List Applications
With so many different ways to filter your proxy list, it’s simple to align your IP addresses with your project’s technical requirements. All that remains is to choose the right one for your application.
Some common examples of proxy list applications include:
- A geography-specific USA proxy list for scraping real estate data
- An elite proxy list to ensure maximum anonymity while conducting market research
- A fresh proxy list to avoid detection while performing competitive analysis
- A private proxy list for high-speed use in Minimum Advertised Price monitoring
- An open/public proxy list for one-off, cost-effective web scraping — while being aware of the risks
- An HTTP proxy list with higher versatility but lower security, useful for copping new sneakers
- An HTTPS or SOCKS5 proxy list for collecting sensitive personal information while remaining secure
- A device-specific proxy list for a website’s performance during web development
Proxies are highly versatile, so this list is by no means exhaustive.
There are plenty of applications for proxy lists, so once you know which kind best suits your project, choose the one that aligns most closely with your security, privacy, speed, and pricing requirements — and always make sure they’re ethically sourced.
Final Thoughts

Proxies allow you to navigate the web and extract the insights you need without compromising your privacy, whether you use them for SEO campaigns, web scraping, or data collection and research. Proxy lists grant you access to a wide number of proxies, and choosing the right one can help you safely scour the web.
At Rayobyte, we offer proxy lists covering a variety of protocol types and locations. We provide data center, residential, and mobile web proxies, all of which are ethically sourced to give you the best chance of avoiding blacklists and blocks. If you need reliable, quality proxy lists and a provider with the skills to support their clients, or if you need help deciding which proxy list is best for you, contact us today.
Looking For Proxies?
Sticky, rotating, residential, data center… whatever you need, we’ve got it!

The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.