The Ultimate Guide To Avoid A Phishing Attack Using Proxies
In the ever-evolving landscape of cyber threats, phishing attacks continue to stand out as a pervasive and formidable scam tactic that malicious actors employ repeatedly. According to Verizon’s 2023 Data Breach Investigations Report, phishing attacks are the second-most common way in which attackers access organizational systems, second only to stolen credentials.
As the cybersecurity statistics indicate, these deceptive maneuvers remain a serious concern for organizations worldwide. The threat actors’ obvious adaptability and adeptness at incorporating current trends into their strategies have left many wondering how to avoid a phishing attack when it seems inevitable.
Let’s define a few types of phishing attacks, examine the risks of phishing attacks, and dig into how you can avoid becoming the victim of a phishing attack using proxies.
What Is a True Phishing Attack?

A true phishing attack is a type of social engineering cyber attack. While conducting a phishing attack, a threat actor poses as a trustworthy entity, such as a colleague or acquaintance, to attempt to deceive individuals or organizations into revealing sensitive information, such as passwords, financial information, IP addresses, or personal identification. They typically do this through deceptive communication, often via email, but can also use text messages, social media messages, or even phone calls.
It can be challenging to avoid a phishing attack. Successful phishing attacks allow cybercriminals to access an organization’s network, which can have a ripple effect that spreads throughout the organization and even onto third parties. Phishing can result in data breaches, identity fraud, data or service loss, or malware or ransomware installation.
The United States Cybersecurity and Infrastructure Security Agency (CISA) describe phishing in this easy-to-understand infographic. The phishing attack process typically involves multiple steps:
1. Creating the bait
The attacker creates fake communication that appears to be from a legitimate source, such as a well-known company, a government agency, a bank, or a social media platform. The communication might contain logos, text, and links that mimic the genuine entity’s appearance.
2. Crafting deceptive content
The attacker crafts a message to instill a sense of urgency, fear, curiosity, or excitement in the recipient. For instance, the notice might claim there’s an issue with the recipient’s account requiring immediate action.
3. Including fake links
The attacker includes links in the message that appear legitimate but actually lead to fraudulent websites. These websites mimic the real ones, fooling the recipient into providing sensitive information or inadvertently downloading malware or ransomware. These believable tactics make it harder to avoid a phishing attack.
4. Collecting data
When recipients click the fake links, they get to the fraudulent website. The page prompts them to enter sensitive information, such as usernames, passwords, credit card numbers, or other personal details.
5. Stealing information
The attacker uses the victims’ information for malicious purposes, such as identity theft, financial fraud, or unauthorized account access. On a larger scale, threat actors can use the information gleaned or malware installed to worm their way into an organization’s network, where they can wreak havoc. This is why it’s essential to know how to avoid a phishing attack in the first place.
What Is an Example of a Phishing Attack?

Phishing attacks come in various forms, each tailored to exploit diverse vulnerabilities or trick individuals into divulging sensitive information. Here are some common phishing attack examples:
Email phishing
What is an email phishing attack? Such an attack occurs when attackers send emails that appear to be from legitimate sources, such as banks, social media platforms, or government agencies. These emails often contain urgent requests to update account information, verify credentials, or take immediate action. Recipients click URLs that take them to spoofed websites, where threat actors collect their data. Often, phishing emails try to deceive recipients into revealing sensitive information, clicking malicious links, or downloading malicious attachments.
Email is one of the most common and effective methods these threat actors use to perform phishing attacks. It is because email is a widely used and accepted communication channel with messages that malicious actors can easily manipulate to appear legitimate.
Attackers often manipulate the “From” field in emails to make it appear that the message is coming from a legitimate source, such as a trusted colleague, an acquaintance, or even a family member. They may also use a domain that appears nearly identical to the genuine URL, which can make it hard for the recipient to avoid a phishing attack.
There are several forms of email phishing, which we will detail below.
- Spear phishing: This is a targeted form of email phishing where attackers personalize their messages using information about the recipient to increase the email’s credibility. For example, they might use the recipient’s name, job title, or other relevant details to make the email seem more legitimate. This allows the scammers to trick the victims, who may be uninformed about how to avoid a phishing attack.
- Whaling: Whaling, also known as CEO fraud, is a form of spear phishing that targets high-profile individuals, such as CEOs or other high-ranking executives within a targeted organization. Threat actors aim to access sensitive corporate information or financial details in whaling attacks.
- Clone phishing: In a clone phishing attack, cybercriminals clone a legitimate email and modify it slightly to include malicious links or attachments. The source appears trustworthy, and these emails often claim to be a resend of a previous legitimate email.
- Attachment-based phishing: In an attachment-based phishing attack, cybercriminals send an email with a malicious attachment, such as an infected document or executable file. When the recipient opens an attachment, that action executes malware on the device.
Voice (phone call) phishing
In a “vishing” attack, threat actors use phone calls to deceive victims into revealing personal information. The attackers might pretend to be from a trusted organization, such as a bank, and ask for sensitive data over the phone.
Text message phishing
Similar to vishing, smishing (SMS phishing) involves sending deceptive text messages instructing recipients to take actions, such as clicking links or providing personal information.
Social media phishing
Social media phishing attacks use social media platforms to send messages or create fake accounts that impersonate friends, family members, or trusted organizations. These attacks aim to trick users into clicking malicious links or providing sensitive information.
URL phishing
What is URL phishing? URL phishing, also known as phishing URLs or phishing links, is a type of attack in which threat actors create deceptive web addresses (URLs). These URLS mimic legitimate websites to trick users into revealing sensitive information or downloading malware.
Threat actors often distribute fraudulent URLs through phishing emails, text messages, social media posts, or other forms of communication. Many victims fail to avoid a phishing attack because the URLs appear to be from reputable sources, which helps trick victims into clicking them.
When users click the phishing URLs, these addresses redirect them to fraudulent websites that look like the real ones. These fake websites mimic the appearance of legitimate sites, complete with logos, graphics, text, and login pages. For this reason, many hapless users fail to avoid a phishing attack.
Below are some examples of URL phishing.
- Pharming: In pharming attacks, threat actors use malicious software to redirect users from legitimate websites to fraudulent ones without their knowledge or participation. They achieve this by compromising Domain Name System (DNS) settings or exploiting vulnerabilities in routers.
- Credential harvesting: Credential harvesting is a phishing attack in which threat actors create fake login pages that closely resemble the login pages of popular websites. When users input their credentials, the attackers capture the information for unauthorized access.
- Malvertising: Malvertising is a type of phishing attack in which threat actors compromise legitimate online advertisements, allowing them to redirect users to malicious websites. This can happen when users click ads that seem harmless.
What Are the Risks of Phishing Attacks?

Phishing attacks pose significant risks to individuals, businesses, and organizations. Here are some of the key risks you face if you fail to avoid a phishing attack:
Financial losses
Phishing attacks can result in financial losses for individuals and organizations. Attackers can steal funds directly from bank accounts, make unauthorized transactions, or gain access to whole financial systems and steal sensitive financial information.
Threat actors can also use phishing attacks to distribute ransomware. This malware encrypts a victim’s data and demands a ransom payment in exchange for the decryption key. If they don’t pay the ransom, the victim may lose access to their data permanently.
Businesses and organizations falling victim to a phishing attack can also face regulatory violations if sensitive customer or employee data gets compromised. This can lead to legal consequences, fines, and penalties.
Identity theft
In phishing attacks, cybercriminals often collect the victim’s personal information, which they can use to impersonate the individual. Attackers may open new accounts, apply for loans or employment, or conduct other fraudulent or even criminal activities in the victim’s name.
Reputational damage
If an organization can’t avoid a phishing attack, its reputation can suffer. Customers may lose trust in the organization’s ability to protect their data, which can cause a loss of both customers and credibility.
Spreading and extended consequences
Phishing emails often contain malicious attachments or links that can lead to malware installation on the recipient’s device. This malware can steal sensitive information, provide remote access to the attacker, or engage in other harmful activities. It can even shut down an organization’s entire network.
Failing to avoid a phishing attack can lead to online account compromise, including email, social media, and financial accounts. Attackers can use these compromised accounts to send more phishing emails, spread malware, or access additional sensitive information.
Operational disruption
Successful phishing attacks can disrupt business operations. Malware infections can slow down systems, cause downtime, and disrupt the normal flow of work.
Employees who can’t avoid a phishing attack might spend time dealing with the aftermath, such as changing passwords, reporting incidents, or addressing security concerns. All this can lead to reduced productivity.
Intellectual property theft
Phishing attacks can target organizations’ intellectual property (IP), trade secrets, and proprietary information. Cybercriminals can use stolen intellectual property for competitive advantage or sell it to the highest bidder.
What To Do If You Fail to Avoid a Phishing Attack

Those who couldn’t avoid a phishing attack should act immediately to minimize the damage. The sooner you take steps to secure your accounts and devices, the less likely you are to experience further damage or loss.
Scan for malware
If you clicked on a link or downloaded an attachment from a phishing email, scan your device for malware using reputable antivirus or anti-malware software.
Change your passwords
If you’ve entered your login credentials on a phishing site, change your passwords immediately for any potentially affected accounts. Make sure to use strong and unique passwords for each account.
But what to do when a scammer has your address? The best course of action is to enhance your physical security. Consider using a locked mailbox or post office box and consult legal counsel to explore potential options for recourse.
Contact the affected institution
If the phishing attack has targeted a specific organization or service (such as a bank or social media platform), contact the company’s official customer support or security team to report the incident and follow their recommended steps.
Monitor your accounts
Regularly monitor your financial accounts, email accounts, and any other online accounts the attack may have compromised. Look for any unauthorized transactions or suspicious activities.
Check your credit
In the U.S., federal law entitles you to a free copy of your credit report from each of the three major credit bureaus every 12 months. You can obtain your reports through AnnualCreditReport.com.
Freeze or lock your credit
In the U.S., you can contact the three major credit bureaus, Equifax, Experian, and TransUnion, and request a credit lock or security freeze. This will prevent criminals from using your stolen information to obtain loans, apply for jobs, etc.
Enable Multi-Factor Authentication (MFA)
Enable MFA wherever possible on your accounts. This adds an extra layer of security by requiring a second form of verification in addition to your password.
Alert your contacts
If you received a phishing email and clicked on a link you suspect is malicious, let your contacts know about your potentially compromised account. Caution them not to click any links or download attachments from emails that appear to come from you during that time. This can help others to avoid a phishing attack.
Check your email filters
Check if your email provider has marked the phishing email as spam or placed it in quarantine. This can help prevent similar emails from reaching your inbox, giving you a better chance to avoid a phishing attack in the future.
Report the incident
Report the phishing attack to the appropriate authorities, such as your local law enforcement or the relevant cybersecurity agency in your country. In the U.S., you can:
- Report a phishing email and forward it to the Anti-Phishing Working Group ([email protected]).
- Report a phishing text message by forwarding it to SPAM (7726).
- Report phishing attacks or attempts to the Federal Trade Commission (FTC) at ReportFraud.ftc.gov.
If you suspect a scammer has your personal information, visit IdentityTheft.gov, which offers specific steps to take depending on your situation.
Update your security measures
Ensure that your operating system, software, browsers, and antivirus programs are up to date with the latest security patches. The FTC website offers an article titled “How to Recognize, Remove, and Avoid Malware.”
Be cautious moving forward
Be extra cautious when interacting with emails, messages, and links. Avoid clicking suspicious links and downloading attachments you did not request. Be careful when sharing personal information online, especially on social media platforms. Avoid providing unnecessary personal details that scammers could use against you.
Educate yourself
Learn from the incident. Understand how the phishing attack occurred and educate yourself on how to avoid a phishing attack in the future.
Attend security awareness training
If you’re part of an organization, attend any security awareness training your employer offers to understand how to detect and avoid a phishing attempt.
How To Identify Phishing Websites

Identifying scam websites is crucial to help you avoid a phishing attack. Here are some steps you can take to recognize fraudulent sites:
- Check the URL: Examine the URL (web address) carefully. Phishing websites often use URLs that resemble legitimate ones but contain slight variations or misspellings. Avoid a phishing attack by looking for typos, extra characters, or domain names different from the official website.
- Look for HTTPS: Legitimate websites use HTTPS (HyperText Transfer Protocol Secure) to encrypt data transmitted between your browser and the website’s server. Check for the padlock icon in the address bar and ensure the URL starts with “https://” before entering sensitive information.
- Verify the domain: Hover your mouse pointer over links without clicking to see the actual destination URL in the status bar or pop-up tooltip. Being cautious if the link doesn’t match the website you expect to visit can help you avoid a phishing attack.
- Avoid pop-up windows: Be wary of pop-up windows that ask for sensitive information. Legitimate websites rarely ask for personal information via pop-ups.
- Check for spelling and grammar: Phishing websites often contain poor spelling and grammar. Look for errors in the website content, email messages, and forms.
- Examine the design: Phishing websites may look similar to the real ones, but they may lack the same level of professional design and branding. Look for inconsistencies in logos, fonts, colors, and layouts.
- Be skeptical of urgency: Phishing websites often create a sense of urgency to prompt you to take immediate action. They may claim your account is in danger or that you must act quickly to claim a reward.
- Don’t click links in emails: Instead of clicking links in emails, manually type the official website’s URL into your browser’s address bar to access the site. It can help you avoid a phishing attack by being sure you are visiting the correct website.
- Beware of download requests: Be cautious if a website prompts you to download files or software. Malicious downloads can contain malware.
- Use safe browsing tools: Enable safe browsing features in your browser or use browser extensions that help identify and block phishing websites.
How To Avoid a Phishing Attack Using Proxies

Cybersecurity firms employ proxies for various crucial data protection purposes in the ongoing battle against malicious actors. But how can proxies help to avoid a phishing attack?
Proxies act as intermediaries between your device and the websites you access. If you suspect an email or communication is phishing-related, a proxy can add a layer of protection to help you avoid a phishing attack. By routing your internet traffic through a proxy server, the proxy hides your actual IP address, making it harder for attackers to target you directly or identify your geographical location.
Proxies also limit the information you expose online by obscuring your IP address. They make it more challenging for attackers to track your online behavior and gather personal data.
Some phishing attempts may involve spoofing legitimate websites blocked in your region. Using proxies, you can access such sites without revealing your IP address, which prevents attackers from monitoring your access patterns and targeting you with region-specific phishing tactics. Ultimately, all these security measures help you avoid a phishing attack more effectively.
Protect Yourself Online With Rayobyte’s Proxies

Anonymity is an essential component of trying to avoid a phishing attack. Because of this, Rayobyte’s world-class proxies are the ideal choice for optimal cybersecurity.
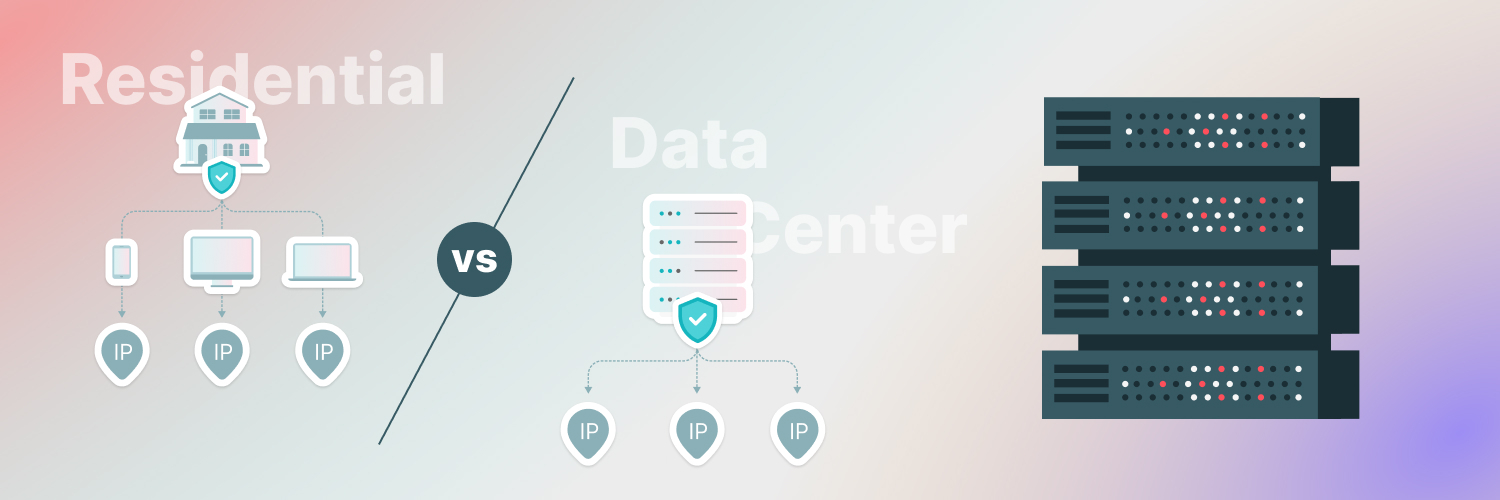
Residential proxies
Residential proxies, assigned by internet service providers, offer heightened resistance to identification and blocking compared to other proxies. These proxies serve as effective safeguards against automated phishing, as they conceal a user’s identity and whereabouts by channeling their data through an ISP’s network.
Because residential proxies utilize IP addresses from genuine home connections, they are less likely to be blocked than data centers or ISP proxies. Despite potentially slower speeds, the anonymity of residential proxies can help you avoid a phishing attack.
Data center proxies
Data center proxies provide quicker connections, but by routing traffic through data centers rather than residential connections, they can be more easily detected. This makes data center proxies more prone to blocking than residential proxies.
An advantage of data center proxies is that they offer faster speeds than residential proxies can because these are hosted on servers rather than home-based networks. Data center proxies might be the right choice when fast connection speeds take precedence over the risk of being blocked.
ISP proxies
ISP proxies make a compromise between residential and data center proxies, delivering speeds surpassing residential proxies while offering more anonymity than data center proxies. Utilizing an ISP proxy could potentially grant users faster connections without compromising anonymity.
Just like with the previous options, consider which features are most important for your specific use case before choosing the proxy.
Final Thoughts

Phishing attacks continue to evolve, and attackers use increasingly sophisticated methods to trick individuals and organizations. Staying vigilant and practicing good cybersecurity hygiene is a crucial part of how to avoid a phishing attack.
By incorporating the world’s most reliable proxies into your cybersecurity arsenal and practicing vigilant online behavior, you can significantly reduce your vulnerability to phishing attacks and enhance your overall online security posture. Sign up for a risk-free trial with Rayobyte today to start your proxy journey.
The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.