What Can Someone Do With Your IP Address? (And How to Protect It)
IP addresses – we’ve all got one* but not all of us understand it.
Me and you though? We’re smart. We know that an IP address is more than just a series of numbers and points. It’s 32 bits of digital identification for your device and, by extension, you.
You wouldn’t put your Social Security Number or passport online for the world to see (please don’t do that) but you also can’t go online without an IP address… so what do you do?
Let’s answer the obvious questions, as you probably guessed from the title.
- What can other people do with your IP address? (Spoiler: not good things!)
- How can they obtain your IP address?
- How can you protect your IP address from criminals and other ne’er do wells?
*At least one. If your computer nerds like us, you’ve probably got more than one laptop, too, right? Mo’ addresses, mo’ problems
Understanding IP addresses
We’re going to recap some basics here, so if you’re already a master of all things IP address – i.e, you know internet protocol is and how to find it yours, click ahead to the “what can someone do with your IP address” section.
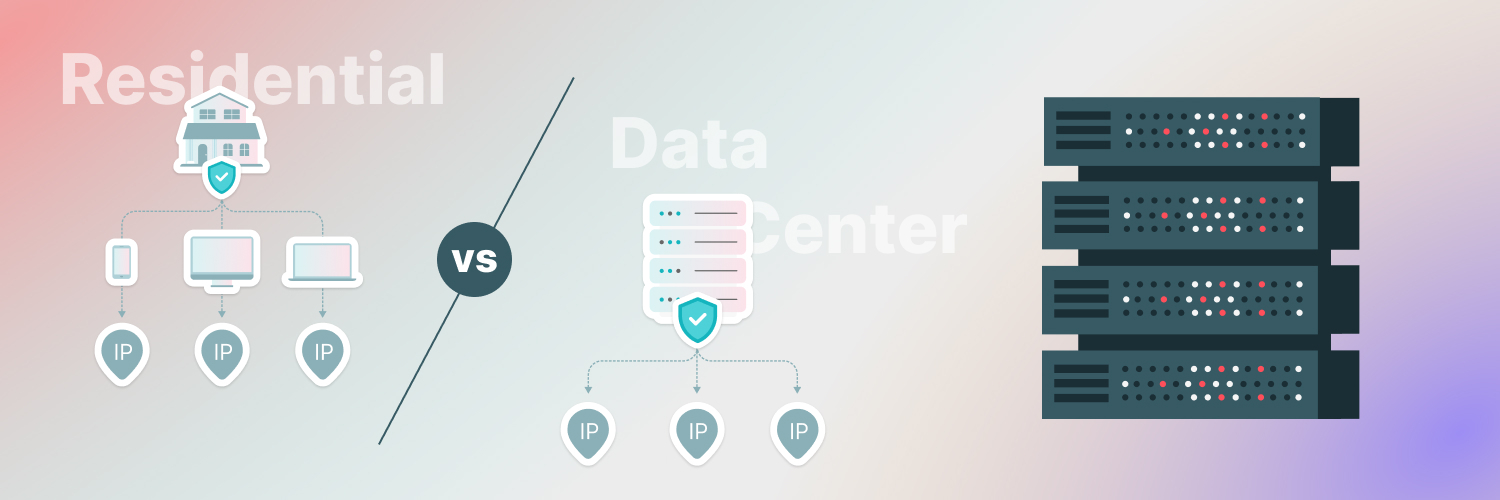
Public vs Private IP Address
When online, your laptop, tablet, phone, smart fridge (we aren’t judging, you browse how you wanna browse!) all have their own IP addresses, but each of these represents a private IP address. They are not exposed when you make requests to other servers, because you’re going through some form of router, which has its own public IP address.

Case closed, right? Far from it. Your home router can still say plenty about you, whilst public wi-fi is generally squeals with the slightest pressure. All private addresses connected can often detect each other, and the wi-fi itself represents a big vulnerability as a result. It’s why you always hear about the danger of public internet.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

IPV4 vs IPV6
Because IP addresses aren’t complicated enough, they also come in two varieties. IPv4 represent the OG IP addresses. They’re the most widely used, but they’ve been around since the 80s. IPv6, with their 128 bits and alphanumeric hexadecimal notations (tech talk for “numbers and letters”), are the new kids on the block.

We bring this up just so you don’t panic if your home address looks different. Most people still have an IPv4 by default, but you might be one of them early adopter types with an IPv6. But we’ve got a whole other discussion on IPv4 vs IPv6 addresses so, if you’re really that curious, go and indulge yourself!
How to Find Your IP Address
You can easily find your IP address through your operating system or device’s settings:
Windows
You can find your IP address in the Network & Internet section of the control panel. For Windows 11, head to “Network Connections” and click on the connection in question. Then, click on “Details…” if it doesn’t show the IP address immediately.
Mac OS
For Macs, go to “System Preferences”, then “Network” and, well… select network. You should see your IP address right here. If not, look under the Advanced options.
Android
Every Android device is a little bit different, so use a little common senses here. Go to “Settings”, look for an “About Phone” or “About Device” section and, from there, head to “Status”.
iPhone
Head to “Settings” and go to the Wi-Fi section. From there, select the active network and scroll down to the part labelled “IP Address”. It’s pretty well labelled.
But What Does My IP Address Tell People?
If after all that, you’re still curious what information your IP address can leak – take a look! We’ve got a free tool to show you exactly what your public IP address says about you. This will show you the sensitive information that your IP address can show but, as we’re about to explain, this could lead to greater personal details if you’re not careful…
So… What Can Someone Do With Your IP Address?
While it might look like a few innocent number, a real IP address can lead to a lot of trouble if it falls into the wrong hands. We know some of these might be extreme, but that’s the internet for you – there’s always someone up to no good.
And one more thing – it’s currently not illegal to trace your IP address. When it comes to legality, it’s all about what someone does with that knowledge.
Track Your Online Activity
If you’re using your real IP address online, then you’re never fully anonymous. Every request you make requires you to ping another server. If someone wanted to trace your online presence, they could look for these pings and determine your activity.
It’s just another reason for using a virtual private network or, better yet, a proxy IP address because, let’s face it, we’ve all got internet activity we want to keep private 😉 And nobody wants targeted ads based on that sort of data.
Track Your Geographical Location
Your IP address isn’t going to give anyone your address, but it does narrow the search down quite a lot with information on your geographic location. It will generally show the city or region you live in (or at least, where your public IP is connecting from) and, from there, someone would only need a few more details, like your name, to find out the rest.
Steal Personally identifiable information
Okay, so we just said that some less than desirable people could use your IP address to find out more details. They could use additional phishing or scamming approaches to learn more, or follow the pings to find what internet sites you use and try to find out more information there. They can spoof your own IP address to get additional information from these sites – and potentially gain access.
Restrict Your Access to Online Services
If someone steals your social security number, it’s not so they can pay your taxes. It’s the same with IP addresses – people aren’t stealing them for philanthropic purposes. This can lead to you getting banned from various websites and online services.
Maybe the hackers were able to gain access, maybe they just used your IP address to spam and DDoS, or maybe they were just bastards that broke the website’s terms and conditions in some form. Either way, that website is angry, and is blocking the only identifier they have: your IP address!
Target You With Spam
We all get enough spam as it is, but there’s a special type of person out there who is just dying to send you more. No, we don’t know why either. IP addresses are another form of identifiable information, as we discussed above.

Through it, people can learn your online behavior and activity. This can then be used to target you with even more annoying online ads and, because crappy people just aren’t crappy enough sometimes, personalized phishing attacks.
Hack Your Devices
This is pretty unlikely – IP addresses are not login credentials – but it’s not impossible either. The most common way of doing this is via ports. Hackers manage to gain access by scanning all possible port combinations for weak links. From here, they could use your computer IP address to send malware to try and take over.
Implement a DDoS Attack
Why would someone even do this? We don’t know either – some people really are just that crap. Your IP address is a key part of your internet connection, so if someone wanted to launch DDoS attacks directly at you, this would be a way to do it.
They could flood your network with as much internet traffic as possible, resulting in distributed denial focused on one singular IP address. It wouldn’t take much, either, since your humble home setup isn’t built to handle vast amounts of inbound web traffic. DDoS attacks really are the worst.
Sell Your IP Address on the Dark Web
We’ve already mentioned malicious ads, personalized spam and other security risks. A stolen IP address can be used for all sorts of illegal activities and, when it comes to this sensitive data, it inevitably ends up on the dark web. The TL;DR is that, once bought and sold, an IP address is likely going to be targeted over and over.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

Commit Criminal Activity via Your IP Address
Yeah, we know – “criminal activity” is quite a general statement. But we’ve done that for a reason – your IP address doesn’t need to be used against you, personally. When tracing illegal online activity, law enforcement often start by tracing IP addresses.

Hackers could route their other illegal activities through your IP address, essentially leaving the cyber trail at your doorstep, rather than theirs.
How Can Someone Find My IP Address?
If someone gets hold of your IP address, bad things can happen. We think we’ve made that clear. So let’s go back a step and answer your next question – how the #%@! do people get hold of IP addresses to begin with?
- By connecting to your network: Join a public wi-fi, and you’re possibly exposed to other IP addresses in the network. We’re not saying that shady guy in your local coffee shop is definitely up to something, but who knows. Use a VPN server or proxy (more on those in a bit!) and avoid the risk.
- Phishing scams: You know these. You’ve won a prize, got a missed package, received an email with a strange attachment. Your IP address is one of the things these malicious links and scripts are after.
- IP leaks: Sometimes you can do everything right and it still doesn’t work. When you browse websites, they often log your IP address on their side. And that’s where IP address leaks typically tend to happen.
- Online activity: The fact is, the more you use the internet, the more your IP address is possibly exposed. Online forums, for example, often log the IP addresses of members, as do online games and more. Heck, even online forms often collect your IP address as part of their own anti-spam measures, which leads to another place your IP address is stored.
Now this isn’t a treatise on the ins and outs of network security, but one thing should be clear: it doesn’t take that much to get your IP address. If someone tries hard enough, and you don’t take basic efforts to hide it, you’ll soon end up with targeted ads, spam and worse.
How Can I Protect My Own IP Address?
The first step is to not panic and put the paranoia away for a sec. There are risks, yes, but hackers aren’t out to get you personally. Instead, such people look to collect IP addresses on a large scale, using a variety of tricks, most of which probably won’t surprise you.

Could you get a new IP address? Yes, but if all your doing is resetting your IP address before going through the same motions, it’s not an effective long-term solution.
So the simple message here is: always use protection! It’s as true here as it is in… other areas of life.
Update Your Firewall and Router
Let’s start with the basics: firewalls serve a purpose. Whilst they don’t encrypt your IP address, they do protect you from malware that could get hold of it. Don’t be a dummy and leave yourself open like this. You’re smart. We trust you.
Be Careful With Public Wi-Fi
We get it, roaming is annoying and a wi fi network is incredibly convenient. But without protections, you can expose private information on the network, including not only access to your online accounts, but also your IP address. And the fake wi-fi hotspot is still very much a scam around the world; if in doubt, stick with mobile data.
Don’t Connect Directly
After all, you only need to expose your IP address once for something to potentially happen, right? And if you’ve made it this far, you’ve probably already determined that is just isn’t worth that kind of risk.
There are a couple of ways to do this, as we all know “never go on the internet again” isn’t an option. The first is to use a virtual private network, also known as a VPN server. Now as a proxy provider, we’d love to tell you that proxies rule and VPNs drool – but somehow we don’t think you’re going to fall for that.

The truth is that a VPN server isn’t that bad. They generally give you a new IP address to mask your real one – and the sensitive information it contains – for the duration of your session, often choosing from a pool of IPs. And for simple browsing, they can be effective.
But proxies? If you want a little more umph, choose a proxy server. With the likes of static, sticky and rotating proxy servers, you have much more control over when to stick with the same IP or get a new IP address each session. What’s more, depending on your needs, mobile and residential proxies can be harder to detect. So if you’re going above and beyond general browsing and access online, consider a proxy over a VPN provider.

Which is ever option you choose, we will say that you get what you pay for. A free VPN service or proxy server is often ‘too good to be true’. Unless it’s a trial for the full product, the chances are the provider isn’t hiding IP addresses very well, and might even be choosing from a very shallow pool when assigning each IP address per session. A free solution rarely protects your sensitive information very well.
Disable WebRTC
Web Real-Time Communication (yeah, WebRTC does sound cooler) technology is designed to enable better real-time communication between web browsers and other apps. The bad news is that it often does that via your IP address so, even if you have a VPN service activated, you should double check this in your browser.
Don’t believe us? f you’re using chrome, just type “chrome://webrtc-internals/” to see any active WebRTCs currently going on.
Can You Get a Dynamic IP Address?
We’ve been talking about static IP addresses primarily, so what about the opposite? We all know dynamic IP addresses are a thing. Since we’re looking to change or mask our public IP address, then you need to ask your internet service provider for a dynamic IP address. But that’s never a guarantee – every Internet Service Provider has a method of IP assignment and you’d need to speak to them to find out more.
A New IP Address from the Router
Most home routers use a Dynamic Host Configuration Protocol, which is fancy talk for automatically assigning new internet protocol addresses. This means you can technically get a new IP address, but its a very clunky and manual process.
Even then, you’ll still send data requests through the new address in the same way so, depending on your needs, it might still be ineffective. In the era of internet traffic, a slow change of the router IP address is the equivalent of a fake moustache.
In Short? Protect Your IP Address!
Your IP address doesn’t tell people everything, but it gives just enough insights to lead to bigger problems. Like many situations, we could tell you its very unlikely to happen, but it could still happen. The internet is a dangerous place, and your IP address is a viable target.
So, do yourself a big favor and invest in protection. There are a few ways to protect your IP address, the most important of which is to hide your real IP address as much as possible.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.