5 Proxy Myths And The Truth Behind Them
There’s a lot of misinformation about proxies that might make you wonder if you should use them or not. Don’t let rumors and false information keep you from taking advantage of all proxies have to offer. Here are five common proxy myths and the truth behind them.
1. Proxies Are Too Complicated

When people start talking about internet protocols and data centers, it’s easy to think proxies are too complicated and best left to techies. While you can geek out and deep dive into proxies, you don’t have to. Like any technology, you can learn as much as you want about proxies or just what you need to know to get up and running.
Most browsers make using proxies pretty simple. If you can follow a simple recipe, you can use proxies.
Scrape at Scale With Chromium Stealth Browser
Self-hosted, Linux-first, compatible with all automation frameworks.

2. Free Proxies Are a Good Way To Get Started

You may think free proxies are a good way to test them without committing to financial investment. However, when it comes to proxies, the rule that “you get what you pay for” applies. There are several reasons you don’t want to use free proxies:
Poor performance
Free proxies are available to anyone, so they’re frequently overloaded and sluggish. Your computer will slow to a crawl while waiting for a response from the server.
Low quality
Because free proxies are used so much, and there are no constraints, they frequently get banned for bad behavior. If someone else used a proxy IP address and was banned from a website, you’ll also be banned when you try to use it. This is referred to as the “bad neighbor” effect and is a significant problem with free proxies.
Security risk
Most free proxies use HTTP vs. HTTPS protocol. HTTP protocol allows your data to be visible during transport to people on the same network as you.
Some free proxies have also been set up deliberately as a Trojan Horse. They can install malware or steal your data when you join the network.
3. Proxies Are Risky

As explained above, there is some truth to this myth, but only if you don’t vet your proxy provider. When you use an ethical proxy provider, proxies are actually more secure because they provide an extra layer of protection between you and the sites you visit. A proxy server acts as an intermediary between you and the internet. Your request goes to the proxy server, gets a different IP address, and is sent to the website. When the website sends a response, it goes to the proxy server before being sent back to you. It helps keep data like your location private.
4. Proxies Are Unethical

In this era of big data, organizations of all sizes, including Fortune 500 companies, government agencies, and universities, use proxies for data collection. While proxies have been associated with questionable practices in the past, Rayobyte has brought proxy use out of the darkness and into the light. We vet our customers to ensure their use cases are ethical and monitor usage to detect any questionable use.
Our ethical practices extend beyond vetting our customers, however. We also set the industry standard for ethical practices in acquiring residential proxy IPs.
Residential IPs are purchased directly from end-users. Some proxy providers acquire residential proxies by hiding a consent clause at the bottom of a wall of text in their Terms of Service or even outright steal them when an end-user downloads a game or app.
At Rayobyte, we ensure that all of our end-users give fully informed consent. They’re also compensated for letting us use their IP addresses, and they can revoke their consent anytime. Finally, we only use their proxy IP addresses when they aren’t using them, and their devices are either plugged in or adequately charged.
5. All Proxies Are The Same

There are multiple types of proxies, and the best type for you will depend on your use case. The main ones you need to know about include:
Data center proxies
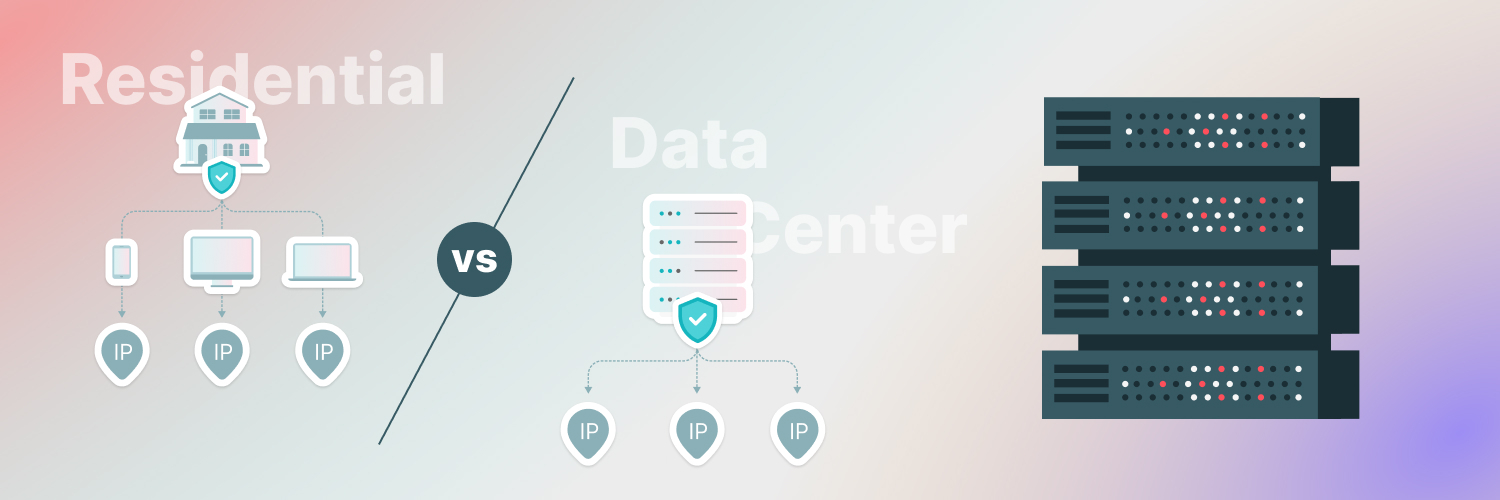
Data center proxies originate in data centers. The main advantages data center proxies have over other types of proxies are speed and price. Data center proxies are ideal for gaming and streaming use cases. The main disadvantage of data center proxies is that they’re easily identifiable as such. Because most people don’t access the internet with a data center IP address, it can trigger anti-bot measures.
Many websites have measures to block data center IPs that display bot-like behavior. Data center proxies may not be the best option if you’re using proxies for web scraping.
If you do use data center proxies, you’ll need a lot of them because they get banned frequently. A rotating pool of data center proxies can help you bypass these bans. Rayobyte’s data center proxies offer maximum redundancy and diversity to keep you up and running.
Residential proxies
Residential proxies are the most authoritative type of proxy you can buy. They’re the best option for web scraping because they are real IP addresses issued by genuine internet service providers (ISPs). Most people access the internet with a residential IP address, so these proxies don’t automatically trigger anti-bot measures. They’re more expensive because they’re harder to source and maintain, but they’re worth it for the extra reliability.
ISP proxies
ISP proxies combine the best of data center and residential proxies. They originate in a data center, so they have lightning-fast speeds. However, they’re issued by ISPs, so they aren’t immediately identifiable as data center proxies. As with our data center proxies, we offer redundancy and diversity to help you bypass bans. If you do get banned, we’ll instantly rotate you to another ASN so you can avoid downtime.
Next Steps With Proxies

There are a lot of proxy myths floating around the internet, but proxies are an essential part of making informed, data-driven decisions. Proxies will give you an edge over the competition by allowing you to collect data for many different use cases without being shut down. Whether you’re building your own web scraper or want to simplify the process with Rayobyte’s Web Scraping API, proxies can help you gather the data you need to run your business more efficiently. Reach out today to find out how we can help you.
Scrape at Scale With Chromium Stealth Browser
Self-hosted, Linux-first, compatible with all automation frameworks.

The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.