The Ultimate Guide to Avoid Phishing Attacks With Proxies
Phishing is a complex and often successful form of cybercrime, intended to deceive victims into sharing confidential information such as usernames, passwords, and credit card details. Although it can take many forms — from email phishing scams to CEO frauds — understanding the different attack types and implementing best practices are essential in forming an effective anti-phishing strategy.
Employees, especially, need to gain a decent understanding of how to avoid phishing attacks as the impact of a successful malicious attack can permeate their organization.
This article explores the various methods attackers use for online phishing campaigns, discussing tips on how to avoid phishing attacks via appropriate user training, automated solutions like DNS traffic filtering or proxies, and implementing proper policies for incident management. Beyond that, it also goes into detail regarding web proxies and how they are used as an anti-phishing defense.
What is Phishing?

Phishing is a sophisticated form of scamming commonly used by hackers to steal confidential information, like usernames, passwords, and credit card information from unsuspecting victims. Attackers mask themselves as credible entities — usually mimicking the look of prominent companies — in an attempt to deceive people into sharing their delicate data.
Scrape at Scale With Chromium Stealth Browser
Self-hosted, Linux-first, compatible with all automation frameworks.

When successful, these malicious third parties obtain access to your private accounts and personal details that can be sold off for financial gain or used against you through blackmail strategies.
It’s extremely important to become familiar with all the various types of phishing attacks available. So, we can protect ourselves accordingly.
Email Phishing
The most popular method of phishing is via email, where attackers send fraudulent messages that appear to come from a trusted source (such as banks, online retailers, or government agencies) with the aim of tricking recipients into clicking on malicious links or opening attachments containing malware.
Spear Phishing
Spear phishing attacks target specific individuals or organizations in an attempt to manipulate them into providing confidential information. Attackers use personalized messages and enticements that appear legitimate to trick people into giving away passwords, banking credentials, and other sensitive data. The attacker may also implant malicious software on your computer when you open the message or download attachments included with the message.
Vishing and Smishing
Vishing and smishing attacks are attempts to get sensitive information from unsuspecting victims. In vishing attacks, attackers use voice-over IP (VoIP) technology such as phone calls or text-to-speech applications to impersonate a trusted source to trick people into revealing private data. In smishing attacks, the attacker uses SMS messages sent via mobile phones with malicious links that encourage the target recipient to click on them and enter personal details, which can then be used for fraud or identity theft.
CEO Fraud
CEO fraud, also known as “business email compromise” (BEC), is a type of phishing attack in which an attacker masquerades as a high-level executive, such as the CEO or CFO. The goal is to trick victims into sending money transfers, wiring funds, or disclosing sensitive information to the impostor. To make their attacks seem more legitimate they often use publicly available information about the company’s personnel and operations.
Angler Phishing
Angler phishing is a type of cyberattack where an attacker sends emails containing malicious links, malware downloads, or fraudulent websites that look legitimate. The goal is to trick the victim into giving away sensitive information such as passwords and financial data.
Watering Hole Tactics
Watering hole tactics are a more sophisticated form of angler phishing. Watering hole attacks are a type of malicious attack in which criminals infect legitimate websites so that when internet users visit the site, their computers will become infected by malware. Cybercriminals select popular websites where they know users often go and plant software code or links to download malicious programs. When unsuspecting victims visit these sites, they can unknowingly give cybercriminals access to their information, leading to viruses like ransomware taking over networks or phishing scams that compromise confidential data.
With that background established, let’s take a look at how to prevent phishing attack tactics.
Phishing Prevention Best Practices

Obviously, the best answer to how to avoid phishing attacks is to prevent the attack from taking place by arming key targets with appropriate information. Another way that’s usually added on top of that is to leverage automated phishing prevention via layers of defense such as detectors for watering holes and angler phishing tactics. Spam filters are already common ways of defending against simple CEO frauds, too.
Still, the foremost phishing attack prevention methods involve best practices surrounding due diligence on the part of the potential targets.
Heightened Security Awareness
So what’s the best way to resolve the question of how to avoid phishing attacks? Increase awareness about how to identify attempts and take steps to protect yourself from becoming a victim. The key element here is providing targeted individuals with information on how these scams work so that they can better spot suspicious emails or links before opening them or clicking through.
Providing online security training offers key personnel an opportunity to stay informed and vigilant against potential threats like phishing scams. Additionally, organizations should prioritize other measures like employee access policies, secure passwords, and company-wide email hygiene practices. This helps protect systems against attack methods like phishing.
Improved Security around High Volume Vectors
To protect against phishing attacks via email — the most popular vector for phishing — you should start by utilizing the existing security tools available in your chosen computing environment. For example, services such as Gmail and Microsoft Outlook feature built-in spam filters that can detect malicious messages before they reach inboxes. Similarly, setting up two-factor authentication for incoming emails adds an extra layer of security to ensure malicious actors are prevented from accessing sensitive information or transmitting malware over digital networks.
To reiterate: user training remains an important part of any anti-phishing strategy — teaching employees how to recognize a suspicious email and use best practices when handling potentially risky content is key in preventing successful attacks on business systems.
Use Solid Antivirus and Firewall Solutions
Resources focused on delivering comprehensive data protection also exist. For instance, investing in a strong layer of malware/virus scanning software provides another safeguard against phishing attempts by detecting dangerous websites or files before they enter company computers.
An antivirus solution is an essential tool, an answer for how to avoid phishing attacks. Standard antivirus tools are designed to scan files in order to detect any traces of malicious code injection or other virus threats, and upon threat detection will prevent the file from executing itself — thereby stopping hackers from delivering their payload into your organization’s network.
Unfortunately, these standard AV solutions may not be enough when it comes to advanced malware and sophisticated phishing attacks. To combat this problem, organizations should invest in a next-generation antivirus (NGAV) with extended scanning features as well as firewall integration capabilities for added protection. NGAVs provide more comprehensive coverage than traditional AVs alone, which makes them the logical choice when trying to protect against increasingly complex cyber threats such as advanced phishing attempts.
Keep Browsers and Online Software Updated
Keeping all your organization’s browsers and highly used software up to date is vital in avoiding phishing attacks. Attackers take advantage of vulnerabilities in outdated programs and applications which can lead to system breaches. So, it’s important that browsers are updated with the latest security patches released by developers. Without these security measures, employees may be left vulnerable even if they aren’t primarily responsible for cybersecurity duties.
To ensure patched safety for each browser used within the company or organization, installing an automatic software updater will close any gaps in existing security protocols as soon as new patches are available after release. The solution idea helps streamline and manage vulnerability while ensuring no employee’s browsing is left unprotected from malicious entities online which might target them via phishing attempts if older software remains unchanged or unpatched on their device(s).
Use DNS Traffic Filtering
A great way to protect people from phishing attacks is by using a DNS traffic filtering solution. Doing this allows you to scan for malicious domains on all incoming and outgoing internet traffic, as well as allows you to log them for review. This gives your organization visibility into where activity appears risky or suspicious in real-time — and can help prevent harm before it happens.
The technology works by scanning domain names against a database of malignant URLs identified through feeds of known threats located all over the web, including darknet sites, open sources such as threat intelligence alerts, and exchanges with industry peers like other ISPs or organizations that use similar tools. Through actionable reports based on these scans, administrators can detect any malicious activity quickly. So, they can be blocked off right away at the source prior to further propagation throughout their network resources. This effort concludes a crucial part in mitigating potential phishing incidents within an organization’s environment.
In addition, many DNS filter providers facilitate integration options that allow synchronizing rules across multiple security layers such as firewalls and web proxies — becoming an important ally when preventing targeted malware attacks from reaching employees’ devices or critical data repositories. These are all necessary measures given the accelerating sophistication levels found in modern attackers’ campaigns motivated especially around financial gains and leading directly towards ransomware (e.g. crypto viruses).
Disable Pop-ups
Pop-ups are one of the most common ways for malicious actors to reduce a user’s security. So, it is important to disable them where possible. Some corporate networks may have already configured this function but, if not, disabling pop-up windows and macro attachments can be done relatively easily via browsers or through anti-spam programs. Disabling these features will limit your access to some online resources as they can be used safely in some circumstances; however, limiting those risks is well worth the effort when considering phishing attacks specifically. Additionally, you can manually filter those resources where needed.
The same goes for macro attachments. While they add a layer of convenience by enabling fully automated functions and processes within documents (think fillable forms), their power makes them an enticing attack vector for cybercriminals who could potentially use macros without explicit permission from users/clients during an email campaign that looks more legitimate than what’s typical among phishing attempts with suspicious links and headers. To mitigate these risks, it’s a best practice that all macros coming from external sources be blocked until further vetting takes place. Preferably, vetting is performed using automated threat analysis tools such as malicious URL scanners before opening any applications attached to emails or other messages sent externally.
Scrape at Scale With Chromium Stealth Browser
Self-hosted, Linux-first, compatible with all automation frameworks.

Implement Proper Policies
Putting in place an effective Incident Reporting Policy is one of the most important steps any organization can take to protect against phishing attacks. To put it simply, no cybersecurity system or employee training program is foolproof. Even when the best measures are taken, malicious actors may still attempt to infiltrate or disrupt operations. When that happens, having a well-defined process for responding quickly will make all the difference.
When setting up a response plan for preventing and mitigating phishing attacks and other cyber threats, start by creating a chain of command within your organization. So, employees know exactly who to report suspicious emails and activities to immediately after notifying their managers or supervisors. Each instance should then be addressed according to this predetermined line of authority. In many cases, this should involve taking any affected systems offline quickly to stop attackers from gaining access to additional data — especially confidential information — while reducing potential damage along with system restoration where necessary (if backed up accordingly, which should also be a priority!). Therefore, implementing an Incident Reporting Policy can help keep organizations safe from these kinds of malicious activities, keeping their sensitive data secure.
How to Prevent Phishing Attacks through Automated Proxies

Proxy servers can be used in various ways to protect against phishing attacks.
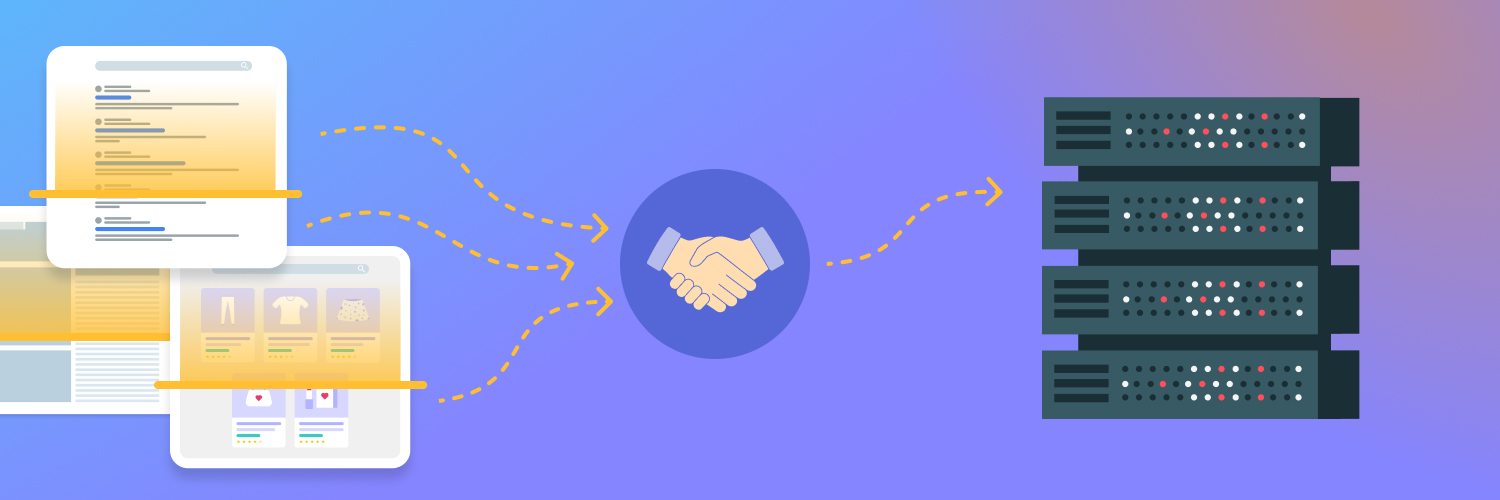
Using a proxy server allows clients on your network to route web traffic through an additional layer of protection before entering the public internet — essentially hiding their true identity from hackers and others seeking unauthorized access. By connecting behind one of these servers, all requests sent by any user are first routed through this proxy server instead of directly out onto the World Wide Web, which helps provide security against phishing attacks by making it much harder for attackers to identify computers connected within certain networks as well as reducing exposure risk individual users face while browsing online. Proxies indeed make for decent spear phishing attack prevention tools.
Additionally, proxies can help provide an additional layer of encryption and almost act as a buffer between computers within your network and any external threats. They help block phishing websites that host malware-laden content from ever loading onto your device in the first place. Proxies also allow employers to block malicious websites without interrupting employee productivity by hiding suspicious sites and only allowing access to safe ones. This is an excellent method of automated credential phishing prevention.
If a user suspiciously receives an email with a link, they can check the source using a secure proxy server instead of clicking on it. In this way, proxies provide effective email phishing prevention.
Indeed, proxy servers are heavily used by cybersecurity organizations in their work.
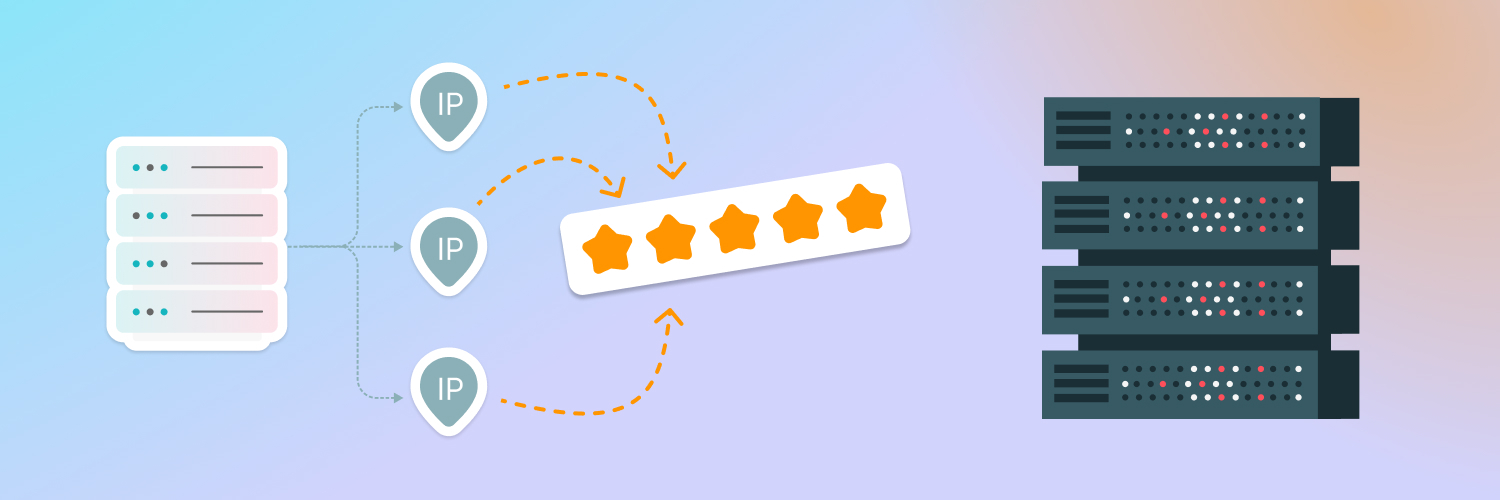
Cybersecurity experts use them to mask their IP addresses as they monitor internal systems, or scan the web for leaked business data. This helps them detect suspicious activity and remain anonymous while providing protection services, like threat hunting. Ultimately, if malicious actors infiltrate proxy servers, the experts themselves are safe.
Organizations can gather more accurate and real-time data with proxies to gain insight into digital threat landscapes, which in turn gives them the ability to scan for vulnerabilities, track assets, and identify misconfigurations faster. Being well-informed on the onset is a step that’s becoming increasingly important due to rising cybercrime numbers. Proxies also help professionals overcome anti-bot measures or region restrictions when gathering large amounts of information from web scraping projects — saving both time and money!
Working with Proxy Server Types for Phishing Prevention

Proxies are crucial for online privacy and security. They hide your IP address, let you access blocked content, and provide businesses with greater control over their activities. Plus, they help small to mid-sized companies scrape data efficiently while keeping servers protected from threats like DDoS attacks or malicious crawlers accessing private info in HTML elements. For larger organizations spread across multiple machines worldwide, proxy networks expand reach quickly without additional infrastructure costs affecting performance throughputs.
In short, proxies matter when you’re serious about protecting confidential data! Of course, choosing the type of proxy to use can be a challenge.
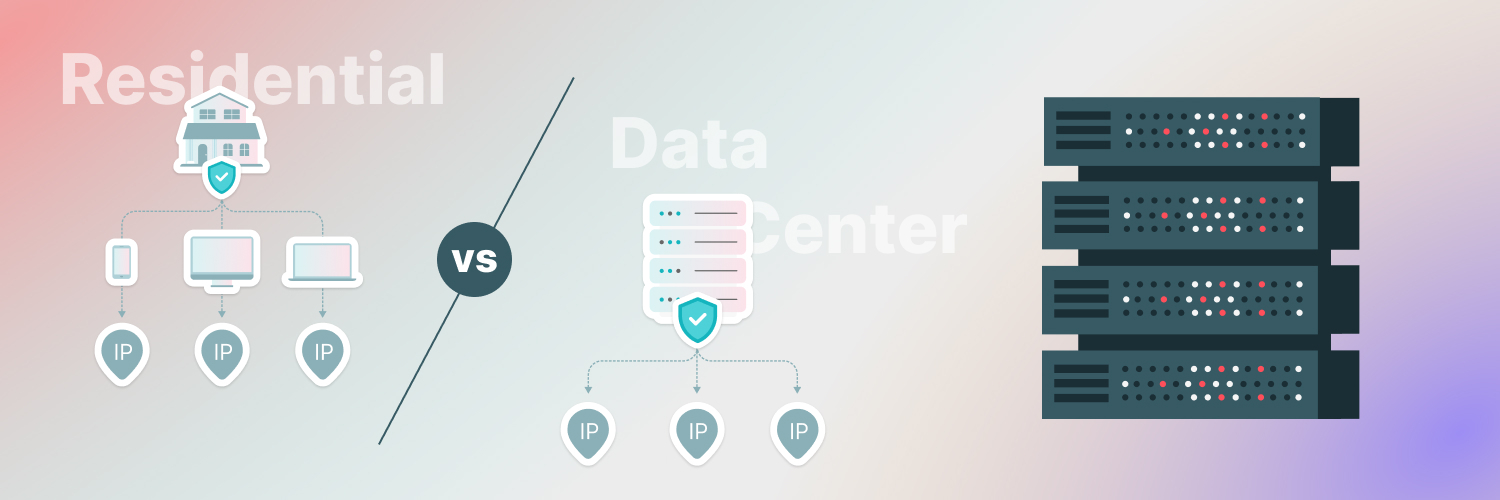
Residential proxies are assigned by an internet service provider, making them more difficult to identify and block than other options — though they may be slower. Residential proxies are an effective automated phishing prevention mechanism as they can help mask a user’s identity and location by passing their traffic through an ISP’s network — making them harder to identify and block. As residential proxies typically have IP addresses from real home connections, they are less likely to be blocked or flagged than data center or ISP-hosted solutions. While residential proxies may be slower than other options, the anonymity provided is beneficial when trying to mitigate phishing threats online.
Data center proxies offer faster connections, but route traffic through data centers instead of homes and can be easier to detect. As they route traffic through data centers, it makes them easier to detect and therefore more vulnerable to blocking than residential solutions. That said, they can offer faster speeds since the service is hosted on a server instead of from home-based networks. Data center solutions may be suitable in cases where fast connection speeds are critical but the risk of being blocked is less important. They can still be useful as an automated defense against phishing attacks so long as you factor in the heightened detection levels when selecting your proxy solution.
ISP proxies provide a middle ground between residential and data centers offering greater speeds than the latter with more anonymity than the former. With an ISP proxy, users may be able to achieve faster connection times for site visits without compromising their privacy. However, as with other types of proxies, it is important to weigh which features are most important when selecting your optimal solution — since connections may vary by ISP depending on location. Ultimately, this can help determine if an ISP proxy makes sense for defending against phishing attacks or not.
Regardless, if any threats infiltrate proxy services — be they residential, data center, or ISP — they would all serve as an additional layer of security for the user. You’re going to have to weigh what features matter most when selecting your proxy solution for optimal protection from phishing attacks. There are both technical and business considerations to take into account before choosing.
When considering the technical factors, some of the most important considerations for choosing a proxy server include:
- Latency – the delay in making or receiving network communications
- Throughput – the amount of data that can be transferred between computers over a period of time
- Authentication requirements – who has permission to access your systems and how they gain access
- Encryption needs – which type of encryption will be needed (e.g. IPsec, SSL) and what level of data security is desired
- LAN and WAN architecture – the types of networks you’re using (wired/wireless) to ensure your proxy server can connect with it all
You’ll also want to consider scalability — will it need to grow with you? Finally, redundancy or failover capability should also be considered, in case one part goes down.
On the commercial / business side, you should consider factors such as pricing structures and licensing requirements. You may need to look at one-time or subscription fees as well as any additional costs associated with ongoing maintenance. Additionally, it’s important to think about how simply your team can manage configuration updates on an enterprise level — is there an easy way to deploy and configure proxy servers throughout your organization?
It’s also important for businesses in highly-regulated industries (e.g. healthcare) or those dealing with sensitive data (e.g. finance) that they comply with relevant laws and regulations around proxy server use.
Finding the Right, Reliable Proxy Servers

When it comes to avoiding malicious actors, enlisting the aid of reliable proxy services like Rayobyte is the answer to how to avoid phishing attacks. Our proxies make resource management much easier and keep you safely disguised from online defenses. Plus, our advanced features and tools can automate certain tasks — e.g. web scraping projects via our Rayobyte’s Web Scraping API. With Rayobyte’s superior protection in place, you’ll be ready to take on any threats that come your way.
Scrape at Scale With Chromium Stealth Browser
Self-hosted, Linux-first, compatible with all automation frameworks.

The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.