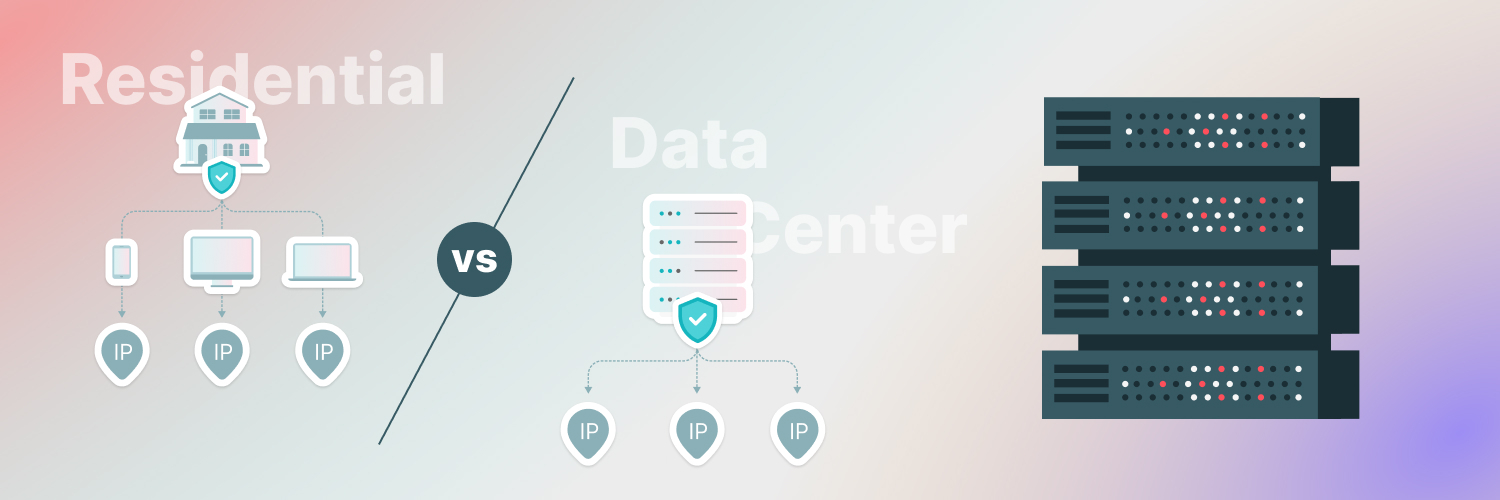
The Ultimate Guide To Using A Fake IP Address
With dire warnings from experts about the state of cybersecurity and the vast amounts of data you create in the context of an ordinary day, wanting to protect your privacy and anonymity on the internet is a natural response. If you’re familiar with the workings of computer networks, you probably realize that your IP address has a lot to do with how your activity is tracked on the web. Faking an IP address can seem like the ideal solution to prevent mega corporations and the government from accessing your personal information.
This article will discuss what an IP address is, how it works, how to get a fake IP address, and why you might want to. If you’re already familiar with a topic, you can use the table of contents to skip around to those that interest you the most.
Can You Fake an IP Address?

You might think faking an IP address is a matter of typing in some random numbers. Unfortunately, it’s a little more complicated than that. There’s no way to fake your IP address. You have to have a valid IP address to connect to the internet at all.
However, there are several different ways you can hide your IP address by using a different one. But before you can “fake” an IP address, you should understand how they work.
What is an IP address?
Your IP address is a unique set of numbers that identifies your device on the internet. You have to have a valid IP address to connect to the internet. IP stands for internet protocol, and it’s a foundational part of how devices communicate on a network. Your IP address contains location information that facilitates communication by allowing the network to differentiate between different computers, routers, and websites.
IP addresses are formatted as four numbers separated by periods, and each number can range from 0 to 255. An organization called the Internet Assigned Numbers Authority (IANA) allocates IP addresses, which are mathematically generated.
How IP addresses work
When you connect to the internet, you first have to connect to a network connected to the internet, which then grants your request to connect. If you’re at home, that’s usually your ISP provider, the same one that issued your IP address. Your internet activity goes through their network, and they route it to you through your IP address.
Your IP address changes when you’re away from home and accessing the internet from another network, such as a coffee shop Wi-Fi. Since you’re using another network, that network will assign you a temporary IP address.
What does your IP address reveal about you?
Your IP address alone can tell someone the city, ZIP code, or area code of your ISP, and it can tell your approximate physical location and the name of your ISP. It doesn’t give away your exact location, but it can be used with your online activity to piece together where you live, work, or go to school.
Why Should You Use a Fake IP Address?

There are many reasons you may want to use a fake IP address. Some of the most common include:
Protect privacy and anonymity
Every time you visit a website, social media platform, or anywhere on a connected network, you leave behind your IP address. All of these sites can access your IP address. Since your IP address doesn’t contain any confidential information, it’s not necessarily dangerous for someone to know your IP address. However, your IP address can be used to track your internet activity, and many people would rather avoid that.
Who might be interested in tracking your internet activity? The following people and organizations may have an interest in tracking your IP address:
Advertisers
Almost everyone has had the experience of talking to a friend or even just thinking about a product, and then an ad for that product appeared in their social media feed. It’s easy to feel like your phone is listening to your conversations or even reading your mind. The truth is a little more complicated.
All of those “allow cookies” banners you click on permit the website to remember details about your visit via first-party cookies. The targeted ads you see usually come from third-party cookies, which work with your visited websites. They are usually marketing firms, and the website grants them access to data about you that it gathers by tracking your IP address.
The marketing companies can build a complete picture of you, including your preferences and what’s going on in your life, by tracking your internet activity across apps and websites. The picture they build can be so complete that it seems to be reading your mind, but that’s just the power of machine learning. Most of us are pretty predictable, and when you can gather such a vast amount of data from millions of people, it becomes pretty easy to figure out what products will appeal to a particular person.
If it creeps you out knowing that some faceless marketer can predict what type of cereal you like, you can effectively opt-out of having your IP address tracked. Using a fake IP address will thwart third-party cookies from monitoring your internet activity.
Employers or schools
If you’re using your employer’s or school’s network, they can see and track your internet activity, including your search history. Some of these networks block access to sites they don’t want you on, while others may allow access but track time spent on them.
Retailers
Your IP address is used to limit what you can purchase when you’re trying to buy limited-edition products from websites that restrict the number of items you can buy. Some retailers also check your geolocation to compare it to the location on your payment method.
Avoid cybersecurity attacks
Bad actors can use your IP address to infect your device with malware. The internet uses ports and your IP address to connect with your device, and there are thousands of possible ports for each IP address. While that sounds like a lot, hackers can use “brute force” — which means trying random ports and hoping to get lucky — to find your port and access your device. Once they have access to your phone, tablet, or computer, they can steal your confidential data, such as your bank account information.
Hackers can also use your IP address to impersonate you for illegal activities. Since law enforcement can use your IP address to track your internet activity, criminals don’t want to use their own. Using your IP address to connect to the internet can make it look like you are the one committing cyber crimes.
Your IP address can be used to “swat” you. One swatting method is when someone uses your IP address to send a threat, such as a bomb threat or an assassination threat, and — boom, next thing you know, a SWAT team is at your door.
Access geo-restricted content
Websites restrict your access to content based on your location for several reasons. These websites use your IP address to identify your location and block you from accessing their site.
Some websites are illegal in some areas, so they are blocked. For instance, online gambling is illegal in Utah, so gambling sites may be barred for residents.
You may be blocked from some content for marketing reasons. Corporations are always looking to maximize their profits, and one way they can do that is by offering different packages and pricing in different areas. You may be restricted if what you want to see isn’t offered in your location.
There may also be licensing issues with some content. A streaming service may only have a license to distribute content in certain countries, so you’ll be geo-blocked if you’re outside of those countries.
Another reason some sites are geo-blocked is because of censorship. Authoritarian governments don’t want their citizens to be able to access information that conflicts with their ideology. In China, almost all social media sites are banned, along with many foreign news outlets. The Chinese government controls internet access in China and restricts, blocks, or deletes information that it considers contrary to the state’s interests.
Regardless of why you’re geo-restricted, the only way to get around these blocks is by using a different IP address. You’ll need an IP address located in a region with access to the content you want to see.
Web scraping
Web scraping is the process of collecting publicly available unstructured data from a website and exporting it into a usable format. You’ll be hard-pressed to find an industry that doesn’t engage in web scraping in some form.
Every day, massive amounts of data are created. You wake up in the morning, log onto your social media account, and click “like” on a political post reflecting your views. On the way to work, you stop for coffee and a breakfast sandwich, and you stop for drinks and hang out with your friends on the way home. You fall asleep streaming the latest episodes of your favorite show.
All of those interactions created a data trail. Combined with the other 7.9 billion people on the planet, that’s a lot of information. Web scraping allows you to burrow through that impenetrable wall of data and find out what you want to know. From life-changing information, such as preventing opioid addiction and overdose, to seemingly frivolous information, like what colors appeal to shoppers on a budget, web scraping can tell you almost anything.
Web scraping allows your business to make data-driven decisions about marketing, product development, customer service, and workforce efficiency. A business without a fully formed data strategy won’t be able to compete in today’s digital-first economy.
However, to effectively scrape the web for data, you’ll need a lot of different IP addresses. Web scraping uses automated technology to gather data faster than humans, and websites install anti-scraping programs to fight web scraping. Using different IP addresses lets you work around anti-scraping measures.
Managing multiple social media accounts
Social media accounts are an integral part of a business’s marketing strategy. You may be managing multiple social media accounts for one brand that wants to segment its audience, or you may handle several different brands’ social media accounts. Either way, you may get blocked if you try to create or access multiple social media accounts from the same IP address.
Shopping bots
Limited-edition products can be hot property in many cases. Nowhere is this more evident than in the “sneakerhead” community. When highly-anticipated shoes are released, they can sell out in minutes. In this competitive market, it’s almost impossible to buy a pair of shoes without using a shoe bot. This automated program monitors and completes the buying process for you.
However, retailers and manufacturers will block any shoe bots they detect, so you’ll need different IP addresses to make your bot look human. A bot can also let you get work around purchasing limits. If the retailer only allows one purchase per household, using a different IP address can allow you to buy more.
Sneakers are the most prominent use of shopping bots, but the same process can apply to buying any type of limited-edition product that sells out quickly. The drop method of releasing products — where a limited amount of the product is hyped and released at a particular time — has become a popular marketing strategy for many brands in the past few years.
How To Get a Fake IP Address

By now, you can see why there’s no such thing as a fake IP address. There are only unused IP addresses and other peoples’ IP addresses. Using an IP address that’s different from your real IP address is the only way to fake one. There are several ways you can disguise your IP address, including:
Public Wi-Fi
When you use public Wi-Fi, the network you connect to assigns you a temporary IP address. There’s never any record of your actual IP address the way there is with other methods of disguising your IP address. Because you never reveal your real IP address, public Wi-Fi is the only way to be completely anonymous.
However, in addition to the hassle of finding and using public Wi-Fi every time you want to connect to the internet, it also poses some serious risks. Public Wi-Fi connections are unencrypted. Although you may be concealing your IP address, you’re revealing a lot of confidential information every time you use one. Anyone on the network can see your data while it’s in transit. Some of the most common ways hackers can use public Wi-Fi to steal your data include:
Fake access points
Hackers can set up fake access points (AP) and trick you into joining their network. This is called an “Evil Twin” attack. A hacker will set up an AP and give it the same or a similar name as the public Wi-Fi you’re trying to join. If you click on the evil twin, all of the data you transmit goes straight through the hacker, including your logins and passwords.
Packet sniffing
Packets are small segments of larger information. Your data is transmitted over the internet in packets. Packet sniffing allows hackers to gather data packets sent across unsecured networks and then use programs to access and read that information.
Man-in-the-middle
Hackers using a Man-in-the-Middle (MITM) attack intercept your communication before it reaches its destination. They can then present you with a website that appears to be the one you were trying to access. When you input your credentials into this website, the hacker will have access to them. You think you’re logging into your bank, but you’re giving cybercriminals your login information.
Virtual private network (VPN)
A VPN can help you hide your IP address and protect your anonymity. It encrypts your data, so you’re not leaving yourself exposed during transit. However, a VPN isn’t a viable solution for all situations where you want to disguise your IP address. When you use a VPN, it’s apparent that you’re using one. It’s like putting on a disguise and telling everyone you’re wearing a wig and a mask.
Additionally, most VPNs use data center IP addresses, so they won’t provide more authority. We’ll go into detail about the types of IP addresses below.
Proxies
A proxy is set up between your device and the internet. However, unlike hacking attacks, the proxy server protects you. When you send a request to a website via a proxy, your request goes to the proxy server first. The proxy server then attaches a different IP address to the request and sends it on. The response goes back to the proxy server, which sends it back to you.
Proxies can be set up with different IP addresses depending on what you need. Proxies are a secure, reliable way to disguise your IP address for various use cases.
How To Fake Your IP Address With Proxies
You can use proxies with every browser and operating system. We’ll walk you through using proxies with Chrome to illustrate how easy it is.
Chrome supports proxies natively, so it’s easy to set up. Here are the steps you’ll need to follow to set up proxies in Chrome on your computer:
- In Chrome, open “Settings.”
- Open the “Advanced Menu.”
- Click “System.”
- Select “Open Your Computer’s Proxy Settings.”
- In the menu that appears, toggle “Look” under “Manual Proxy Setup.”
- Select “Use a Proxy Server.”
- Enter the IP address and port number provided by your proxy provider.
- Save and close your settings.
To set up proxies in Chrome on your Android device, follow these steps:
- Go to Android system settings.
- Tap “Network and Internet.”
- Select “Mobile Network.”
- Click “Advanced.”
- Click “Access Point Names.”
- Click to edit.
- Enter the IP address, port number, and, if needed, your user name and password provided by your proxy provider.
- Save your changes and exit.
- Turn mobile data off and back on again.
- Open Chrome and enter any additional authentication info if prompted.
Why You Should Avoid Free Proxies To Get a Fake IP Address

Free proxies are readily available on the web. You may think they’re the perfect solution. After all, who wants to spend money when they don’t have to? Unfortunately, the adage “you get what you pay for” rings true with free proxies. That free proxy may end up being quite expensive. Some of the significant problems with free proxies include:
Security
It’s expensive to run a proxy server. If you’re not paying for it, someone else is, and not out of the goodness of their heart. The owner of the proxy server has to be making money somehow. The best-case scenario is the proxy provider is making money by putting ads on their site. The worst-case scenario is that hackers set up the proxy network to put malware on your device.
When you use their proxies to protect your privacy, you send them all your personal information and give them access to your device. Even if a hacker doesn’t run your proxy server, it may still pose serious security risks. Most free proxies use HTTP connections instead of HTTPS. HTTP is an unencrypted connection, meaning your data is exposed to others on the network during transit. And if it’s a free proxy server, there are probably a lot of other users on the network.
Speed and performance
Because so many users access free proxies, their servers are overloaded and sluggish. Expect to spend a lot of time waiting. Additionally, when you finally get to use a proxy, you may find you’ve been banned due to the “bad neighbor” effect of bad behavior from a prior user.
Monitoring
Free proxies can be set up as a honey pot so the providers can monitor your connections. Some hackers set up proxy servers precisely to monitor the users. Even if the proxy provider didn’t set up the network specifically to monitor you, the lack of an HTTPS connection means anyone using the network can.
Malware
In addition to the risk of having your data stolen or your connection monitored, free proxy servers may inadvertently infect your device with malware. Proxy servers often sell ad space to generate income. Some malware developers use ads as a vehicle to deliver malware. When you click on an ad, you download the malware. The proxy provider may not even be aware this is happening.
Types of Proxies To Fake an IP Address

There are many different ways to classify proxies. We’ll go over some of the most important features so you can decide which ones are best for your needs.
Data center
Data center proxies originate and are stored in data centers, which house computer networks, systems, and components. Data center proxies are the fastest proxies you can buy. If you’re using proxies for gaming or speed is the most important factor, data center proxies can be an excellent option.
If you’re using proxies for web scraping or another use case where authority is the biggest concern, data center proxies may not be your best choice. Because of their format, data center proxies are easily identifiable as being data center proxies. Most ordinary users don’t access the internet with data center proxies, so this can trigger suspicions on some websites.
Some websites completely block data center proxies from accessing their content. Others may allow data center IP addresses, but they will block the entire subnet if they detect suspicious activity. You’ll be permanently banned if all of your proxies are located in the same subnet.
Rayobyte’s data center proxies provide maximum redundancy and diversity. We offer 9 ASNs, so if one is blocked, we’ll rotate you to another one. With over 300,000 IP addresses and 20,000 unique C-class subnets, you’ll be able to get back up and running quickly after a ban. We have data center IP addresses in over 26 countries so that you can choose your location. Unlimited bandwidth and connections and free replacements let you make as many connections as you need.
ISP
ISP proxies are similar to data center proxies, but ISPs issue them. This gives them much more authority than data center proxies, but they still have the same great speed and performance. They’re harder to detect than data center proxies since it’s not apparent that they are housed in a data center. ISP proxies can be a perfect option for when you need the authority of an ISP-issued address and the speed of a data center IP address.
Rotating ISP proxies let you use a different proxy for each request. This enables you to mimic human behavior and means you’re less likely to get banned. At Rayobyte, we partner with well-known companies such as Verizon and Comcast to provide you with the most diversity. We have five ASNs in the most high-need cities.
Residential
Residential proxies are the most authoritative type of proxies on the market. These IP addresses belong to actual end-users and are issued by ISPs. This is the type of IP address most people use to access the internet, so they don’t raise any red flags when you use them. Residential proxies are ideal if you need proxies to bounce or spoof our IP address.
Residential proxies are sourced from end-users, so it’s a more complicated process than buying them from a data center, which is one reason they’re more expensive than data center proxies. You can tap into a network of millions of devices worldwide to make your connections appear more authentic. Residential proxies are less likely to trigger CAPTCHAs than ISP or data center proxies.
Ethically sourcing residential proxies can be complex. At Rayobyte, we set the standard for ethically sourcing residential proxies. We make sure that our end-users give their full and informed consent. They can easily revoke their consent at any time. We further protect end-users by only using their IP address if their device is:
- Connected to Wi-Fi
- Not being used
- Plugged in or at least 50% charged
Many other companies claim to source their proxies ethically, but they bury their consent agreement in long-winded TOS that no one reads. We don’t believe that’s enough. Proxies have long been associated with gray and black hat practices, but Rayobyte is bringing proxies into the light. Our proxies are used by government agencies, Fortune 500 companies, and small businesses.
Our commitment to ethics doesn’t stop with sourcing residential IPs. We also vet our clients to make sure their use cases are aboveboard. Our customers go through a rigorous vetting process to make sure we know who they are and what they do.
Rotating vs. static
A static proxy is one IP address used in place of your actual IP address. You’re basically exchanging one IP address for another. Static proxies are helpful if you’re trying to bypass geo-restrictions or you don’t want your real IP address tracked.
Rotating proxies are a pool of proxy IP addresses changed at regular or random intervals. They may change after a set amount of time or rotate with each request. Rotating proxies are especially useful if you’re web scraping and need to bypass anti-bot technology.
Shared vs. dedicated
Dedicated proxies are reserved for one user, while shared proxies are available to multiple users. When sharing proxies with multiple other users, you may run into some problems. Overloaded proxy servers can be sluggish and poor performing. You may also run into the bad neighbor effect and have trouble accessing the sites because of previous bans. As with free proxies, widely shared proxies can also have security concerns.
When using dedicated proxies, you don’t have to worry about poor performance or the bad neighbor effect. Dedicated proxies are the most secure, but they’re also the most expensive.
Semi-dedicated proxies can be a good compromise. Semi-dedicated proxies are shared between two or three users. If you work with a trusted proxy provider who carefully vets clients, semi-dedicated proxies can be almost as secure and efficient as dedicated proxies.
Proxy anonymity
Another method for classifying proxies is by how much anonymity they provide. Some proxies provide much more anonymity than others.
Transparent proxies
Transparent proxies don’t hide your IP address at all. Schools or companies might use transparent proxies to restrict access to certain websites, and you may not even realize you’re using one. They’re generally set up by the network owner, not by individual users. Transparent proxies aren’t very useful if you’re concerned about privacy and anonymity.
Anonymous proxies
Anonymous proxies change your IP address, offering more anonymity than transparent proxies. However, when you use anonymous proxies, it’s still apparent that you’re using a proxy. The websites you visit may not be able to identify your actual IP address, but they can tell you’re using a proxy. This isn’t normal user behavior, so it can raise alarms. Some websites don’t allow you access to their content if you’re using a proxy.
Elite proxies
Elite proxies are the most secure type of proxy. They hide your IP address and that you’re using a proxy. They delete the headers that reveal your connection is being forwarded from a proxy server. As far as anonymity and privacy, elite proxies are the best option. All of Rayobyte’s proxies are elite proxies, so you’ll have the highest level of protection possible.
How To Avoid Detection When Using a Fake IP Address

If you’re faking your IP address, you’ll want to avoid being noticed by the websites you visit. Here are several ways you can blend in and avoid software designed to detect fake IP addresses:
Use elite proxies
Elite anonymous proxies are the only proxies that hide your true IP address and hide the fact that you’re using proxies. When you’re buying proxies, ask your provider if they forward the X-Forwarded-For and Via headers. These headers are giveaways that you’re using a proxy.
Use a pool of proxies
If you’re using proxies for web scraping, use a rotating pool of proxies to avoid detection. Changing your IP address with each request will reduce your chances of being blocked by anti-bot software. Web scrapers issue requests far faster than humans can, which is how many bots are detected. Most websites have code that will automatically block an IP address that sends too many requests.
Using a different IP address for each request mimics normal human behavior. If you send 100 requests, a rotating proxy pool will attach a different IP address to each request. This makes it look like 100 different users are each sending one request instead of one user sending 100 requests.
Randomize your activity
Humans are random. They click on something, look at it, click on something else, get distracted, and return a few minutes later. If you’re using a bot, randomize its activity and don’t set it up to work as quickly as possible. Set delays and program random intervals into your requests to make your bot appear more human.
Use the right type of IP address
Data center IP addresses aren’t used by most people. If you want to appear to be a regular user, you need to use the correct type of IP address. Since most internet users access the web with residential IP addresses, they’re your best bet for avoiding detection. Rotating residential proxies are even better since every connection will appear to come from a different residential device.
Using a Trusted Proxy Provider

A lot is riding on your proxy provider, so choosing the right one is a serious decision. When you buy proxies, you’re trusting your provider to protect your data and reputation. You want to be sure your proxy provider is ethical and reliable.
Rayobyte is the largest U.S.-based proxy provider. Government agencies and Fortune 500 companies trust us for their data gathering and aggregating needs. We are proud of what we do, and no one will go further to help you achieve your goals. We offer the most reliable proxy service you can buy, backed by a team of professionals, a dedicated end-to-end infrastructure, and 24-hour customer service.
Final Thoughts

You can’t fake an IP address, but you can use an unused one to disguise your true IP address. There are a lot of benefits to masking your IP address. Malicious actors can use your IP address to steal your data or impersonate you while engaging in illegal activities. Marketers can legally track your internet activity to target advertising based on your history. If you want to guard your privacy and opt-out of personalized marketing, hiding your true IP address with a proxy address lets you do that.
If you need to hide your IP address to gather and analyze publicly available data, proxies are even more vital. Using a pool of rotating proxies allows your web scraper or bot to mimic human behavior and avoid automatic bans. There are many types of proxies available, and understanding the features of each will help you decide which is best for you.
No matter what type of proxy you need, Rayobyte has the most reliable and trustworthy proxies on the market. Reach out today to find out how we can help you.
The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.