Getting An Email Proxy For Security And Peace Of Mind
Since their invention in the late 1990s, emails remain the leading method of communication for American and international businesses. This comes as no surprise, considering they’ve always been, fast, secure, and efficient at conveying information and news — both among the staff of the same business and as external communication with clients and partners.
But in the age of digital advancement, cybercrime and digital attacks are gaining momentum as more critical business data moves to digital mediums — one of which is email. But fear not. Emails aren’t going away anytime soon. There are multiple ways you can boost the security of your internal and external emails without having to uproot your entire communication system. One of the simplest, yet efficient and secure solutions to implement is using proxies for email protection.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

What Are Proxies?

There are many ways you can define proxies depending on their type and use cases. But in general — and in the context of email security — proxies are an intermediary, or middle-man, server that enables you to connect your device indirectly to an internal or external network.
Every time you connect to the internet using a proxy, your internet traffic makes a detour. Instead of directly communicating with the target server, your data is rerouted from your device and into a secure proxy server that encrypts your data and assigns it a different IP address. The server does the same thing to any incoming data. It receives it on your behalf and encrypts it before it sends it to your device via a secure channel.
There are two types of proxy servers depending on their location, IP addresses, and how they receive and encrypt internet data and traffic.
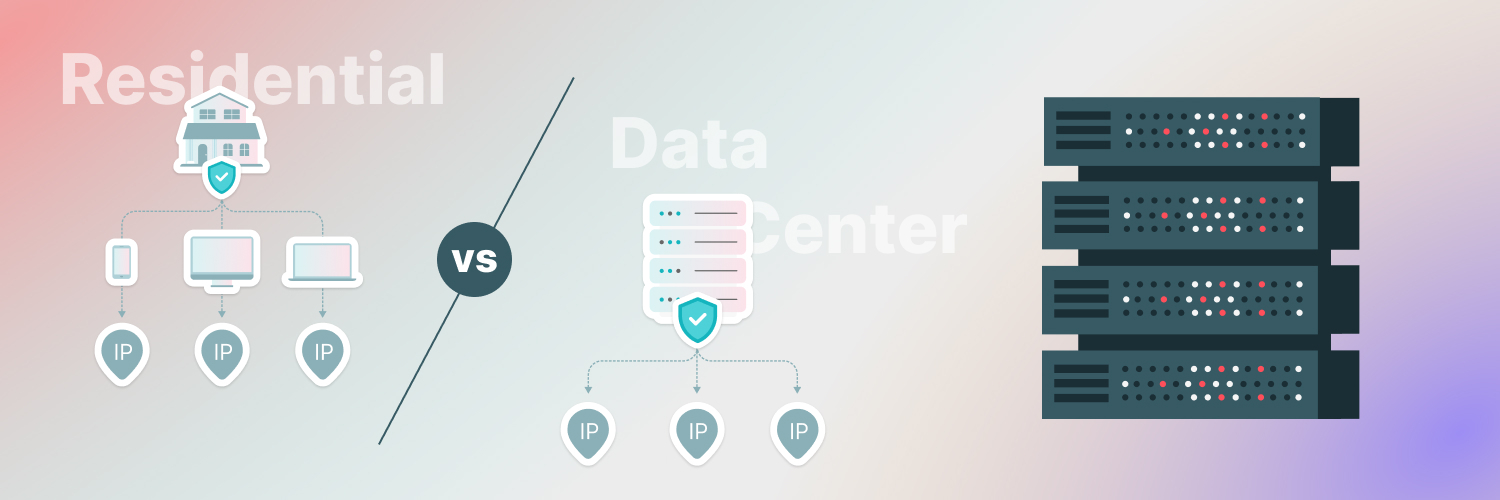
Residential proxies
Residential proxies, as the name suggests, are proxy connections that originate from residential IP addresses. That means the IP address this type of proxy server assigns you is similar in properties to an IP address you’d have with an active internet connection in your own home. Proxy providers often acquire residential proxy IP addresses when homeowners and local residents no longer use their internet connection and sell their IP addresses.
They excel when it comes to providing users with anonymity and believable fake IP addresses. Residential proxies are used most in location and identity-sensitive internet operations like web scraping, ad verification, and marketplace monitoring. When using a residential proxy, you appear to any network monitor like a local internet user and not a bot or a foreigner accessing the server remotely.
When sourced ethically, residential proxies offer more security — with their full consent, a company will pay a person to use their IP address. They will then only allow paid users to access and use these proxies.
Data center proxies
Data center proxies are the most common type of proxy server. In fact, they might be the type you’ve used before when running a VPN either to access geo-restricted content or protect your online privacy and security. They work the same way as residential proxies, rerouting your web traffic and encrypting it before sending it out into the open internet, and vice versa with incoming traffic.
The main difference with data center proxies is the type of IP address they provide. While residential proxies are real, local addresses, data center server’s addresses are artificial and aren’t registered under any real person’s name. Data center proxies are suitable for web browsing that requires high connection speeds like watching streaming services or downloading or uploading massive amounts of data to and from the web.
The only downside of Data center proxies is that they’re more prone to banning than residential IPs. Since they aren’t registered and multiple end-users go through the same server and use the same IP address, websites can flag them as bots and ban them. As a result, Data center proxies aren’t ideal for web scraping, emails, and user and ad verification.
Shared or private?
Both residential proxies and data center proxies can be either shared or private servers. Shared proxies are proxy servers that are shared among various users and corporations. They can be public and available for anyone to use, or paid and shared between a smaller number of users. They’re usually much cheaper to rent out than private servers, but you don’t get to use the full capacity of the server and they aren’t as reliable, making them less than ideal for delicate online operations.
Private servers, on the other hand, are proxy servers that are dedicated fully to you as a user or corporation. They’re far more secure as you won’t be sharing the server space with anyone else. You also get to use the full capacity of the server, allowing for optimized internet download and upload speeds. However, all of those advantages more often than not come with a higher price tag.
Depending on your proxy vendor, you may have multiple options and availability of both types. Rayobyte, for instance, offers both residential and data center proxies in a variety of plans ranging from personal to enterprise and shared to private. To learn more, visit Rayobyte’s Products page that lists out the solutions for success.
Why Do Corporate Emails Need Proxy Protection?

Since corporate emails are the primary mean of communication, not securing them is akin to conducting business meetings and sharing documents on a live stream on a public social media account. There are multiple ways your corporation’s official email addresses could be compromised without adequate protection.
Hacking
One of the biggest cybersecurity breaches of the decade was the hacking of the email of Amy Pascal — the Chairperson of Sony Moving Pictures entertainment Group — in the mid-2010s. The hack resulted in multiple of Pascal’s personal emails being released to the public. And while the damage in this situation was mostly limited to Amy Pascal’s reputation, this incident served as a wake-up call to corporations worldwide to safeguard their emails in fear of similar incidents.
By acting as the middle-man in all interactions between your device and the internet, proxy servers prevent anyone from directly reaching your device and accounts and exploiting any existing vulnerabilities. Additionally, while most email services already encrypt the messages with end-to-end AES 256-bit encryption before sending them, they’re not all security geniuses. Proxies encrypt your entire web traffic, making it twice as hard for any hacker to find their way into your email or deduce a security vulnerability from your general web browsing and online work.
Phishing attacks
Phishing attacks through email make up 90 percent of all cyberattacks aimed at corporations. Not to mention, phishing attacks are getting harder spot even by a trained eye, leaving your company’s email addresses vulnerable to any hacker who knows the address. Even if you or one of your employees ends up falling for a phishing scheme, using a trustworthy proxy could significantly minimize the damages.
If an employee accidentally gives the infiltrator access to the system, the attacker’s traffic still needs to go through the proxy server, which can detect the unusual connection and alert the network’s security admins before the attacker can compromise any sensitive information. In most cases, attackers don’t even know there’s a security proxy standing between them and the email, leading them to let down their guard and even expose their identity to digital forensic investigations later on.
Business email compromise
A Business Email Compromise (BEC) attack is a common cyber threat where the attacker gains access to your email servers and impersonates your corporation’s official name. They’re then able to send legitimate-looking emails to clients and customers asking them for confidential information such as passwords and financial information — depending on the industry and nature of work.
BEC attacks can target both individuals and corporations. While there are multiple ways hackers can gain access to an official email address, the most common is phishing. Once successful, the attacker can use your company’s name and email to scam clients and users alike, leaving your reputation in ruins — especially if you didn’t have cybercrime insurance or it took your IT department a long time to figure out.
Another issue is falling for a BEC scam yourself. One of your partner’s emails could be compromised, which could lead to a much easier and straightforward phishing attack that only reliable proxy servers detect and alert you to.
Internal threats
While unfortunate, internal threats are an inevitable part of any organization regardless of size or industry. An internal threat is any malicious activity that originates in your company. Internal threats can come in the form of an intruding employee looking to leak critical company information for personal gain. And while proxies can help detect and prevent such attacks, those are mostly mitigated using network monitoring.
Scrape at Scale With Chromium
Playwright-compatible. Self-hosted. Built for real infrastructure.

But even the most advanced endpoint detection and protection systems fall short if the threat is spreading inside the network and isn’t leaving its parameters. The easiest way a malicious employee can spread a virus, ransomware, or spyware company-wide is via email. Coworkers naturally trust internal emails and immediately open and download any links or attachments. Emails protected by security proxy get scanned for any suspicious materials and send out an alert if someone was trying to gain access to your internal network via an email.
How to Protect Your Email With Proxies

Proxies can seem complex at first glance. They vary in efficiency, security, and reliability depending on the type you decide on using and whether or not it fits with your goals. However, when it comes to emails, four elements should be present in whatever type of proxy you employ.
1. Encryption
Encryption is the process of distorting data beyond recognition by following a specific algorithm. The goal is to prevent any unauthorized individual from viewing the data even if they intercept it. When getting a proxy, it’s important to know the types of encryption the vendor provides and whether they’re sufficient for your email security needs.
2. Monitoring
Since proxy servers sit at a privileged location where they can monitor and scan incoming and outgoing data, they could be great tools for detecting cyberattacks by alerting security admins to unusual upload or download rates. However, some cybercriminals are sneakier than others, move data at a rate just under the radar, and need specialized monitoring.
Some proxy vendors offer security monitoring services that work alongside your IT and cybersecurity departments. The aim is to find a monitoring system that matches the level of threat your company in general — and emails in particular — are prone to.
3. Privacy
Privacy is an essential part of running a corporation even if it doesn’t affect the security and longevity of your company. Since all of your data is going to pass through a proxy server, the vendors technically are capable of viewing the data and keeping logs of your online actions and exchanged data records.
Before jumping on the cheapest proxy provider you see, make sure the provider has high privacy standards and a strict no-log policy unless it’s an agreed-upon part of your monitoring and security plan. One example of a trustworthy residential proxy provider is Rayobyte — we pride ourselves on having the most ethical cybersecurity solutions. You can learn more about how we set the bar for ethical residential proxies and continue to improve our systems to meet all our customers’ safety concerns and needs.
4. IP address reliability
Emails are an excellent way to communicate with clients and partners, but if your proxy IP address always gets banned or branded as spam by other email service providers, you could miss out on countless business opportunities and revenue due to unreliable communication. Your proxy server provider needs to have a reputation for quality IP addresses that were never involved in any shady or malicious online behavior. Anything less, and your emails might end up getting flagged.
Why Work With Rayobyte?

Rayobyte is a company that dedicates itself to reinventing proxies and providing them as services to everyone who needs them. We believe proxies are an incredibly valuable piece of tech that’s often misunderstood or overlooked by many companies and individuals. While we play in multiple fields, Rayobyte has two main products: data center proxies and residential proxies.
Get started today with the best proxy program from Rayobyte. We only approve organizations and companies that have the same level of authenticity and ethical work operations as themselves — giving you the highest level of ethics and security.
The information contained within this article, including information posted by official staff, guest-submitted material, message board postings, or other third-party material is presented solely for the purposes of education and furtherance of the knowledge of the reader. All trademarks used in this publication are hereby acknowledged as the property of their respective owners.